In today’s world, having a secure, encrypted, point-to-point channel through which your data can travel from a specific location to the cloud contributes to a safer solution if you want to avoid breaches and data loss. There are different ways to allow multiple locations to establish secure connections with each other over a public network, such as the internet-like user-based-authentication VPN, IPSec site-to-site technologies, and other third-party application options.
This blog post explains how to create a secure and encrypted IPSec site-to-site tunnel between Oracle Cloud Infrastructure and another third-party cloud provider like Amazon Web Services (AWS) by using Libreswan. Oracle Cloud offers native cloud VPN functionalities for AWS, Google, and Azure. Alternatively if you’d prefer to use a network virtual appliance like libreswan to establish the VPN then continue reading this blog. This process can also be used with Oracle Cloud Infrastructure Classic and other cloud platforms like Microsoft Azure, or to connect to your own on-premises data centers. In addition to that, the Oracle Cloud Infrastructure (OCI) Site-to-Site VPN service offers a secure IPSec connection between your on-premises network and a virtual cloud network (VCN). You can also use Site-to-Site VPN to connect OCI resources to other cloud service providers like Google Cloud Platform (GCP). Minor adjustments to the steps, below, might be required for other cloud providers.
Getting Started
The following components are the main requirements for enabling a secure channel between Oracle Cloud Infrastructure and an external third-party network:
- Provision and configure Oracle Cloud Infrastructure dynamic routing gateways (DRGs) and customer-premises equipment (CPE) through the dashboard
- A third-party cloud Libreswan instance
- There is no need of additional hardware
Configuration Diagram
The following diagram illustrates this configuration:
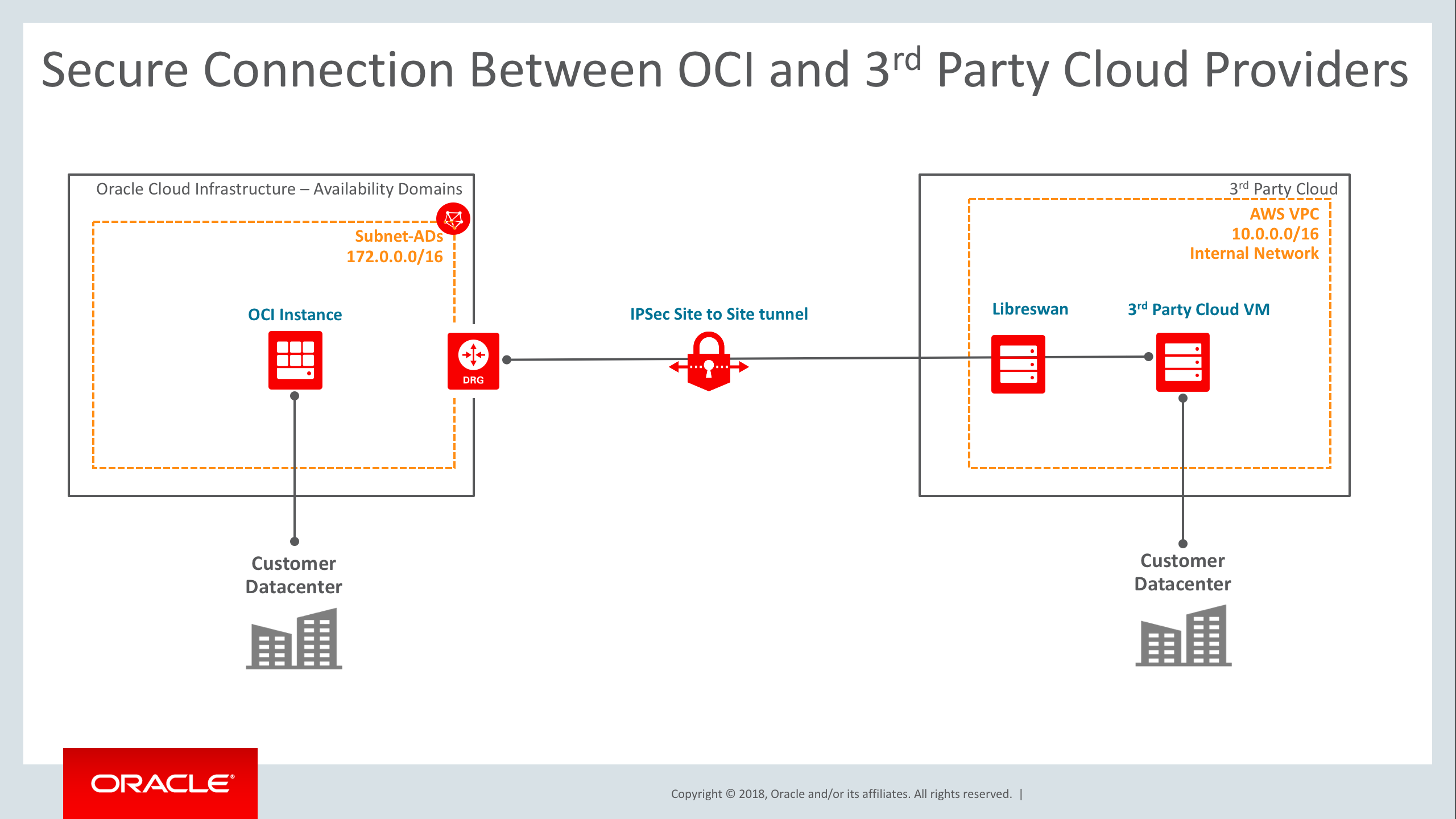
Configuration Process
At a high level, these are the steps required to create a secure and encrypted IPSec site-to-site tunnel between Oracle Cloud Infrastructure and another third-party cloud provider by using Libreswan. Our example uses AWS as the third-party cloud provider:
- Architecture Review.
- Provision an AWS Libreswan VM.
- Start the Libreswan configuration.
- Configure AWS network rules.
- Configure the Oracle Cloud Infrastructure DRG and CPE.
- Configure the Oracle Cloud Infrastructure network rules.
- Configure the Oracle Cloud Infrastructure route information.
- Finish the AWS Libreswan configuration by using Oracle Cloud Infrastructure information.
- Test the IPSec communication between Oracle Cloud Infrastructure and AWS.
Architecture
Libreswan uses the terms “left” and “right” to describe endpoints. Left is going to be represented by Oracle Cloud Infrastructure and AWS for right.
The following table shows how to set up these components:
| Left Side: Oracle Cloud Infrastructure DRG/CPE |
Right Side: Third-Party Cloud Provider Libreswan VM |
| VCN: 172.0.0.0/16 |
VPC: 10.0.0.0/16 |
| DRG Public IP: 129.146.13.53 |
Public IP / ID: 34.200.255.174 / i-016ab864b43cb368e |
| CPE |
Internal IP: 10.0.0.10 |
| Location: Oracle Cloud Infrastructure – US-Phoenix-1 |
Location: Amazon Web Services (AWS) – US East (N. Virginia) |
Configure Libreswan on the Third-Party Cloud Provider (AWS, Right Side)
- Create a Libreswan VM on AWS by using its provisioning process. Use Oracle Linux, CentOS, or Red Hat as the main operating system.
- After the new instance starts, connect to it through SSH and install the libreswan package.
$ sudo yum -y install libreswan
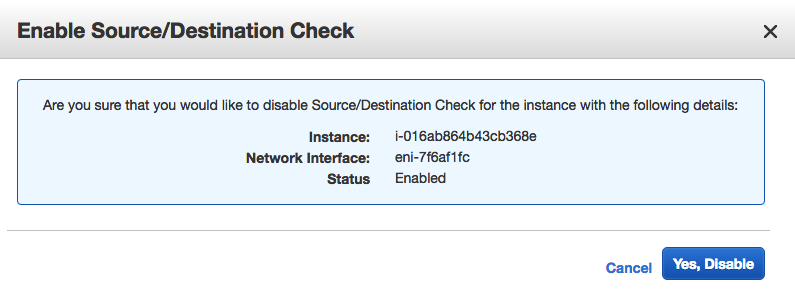
- Disable source and destination checks on the Libreswan VM instance by right-clicking the instance in the console, selecting Networking, selecting Change Source/Dest. Check, and then clicking Yes, Disable.
- Configure IP_forward to allow AWS clients to send and receive traffic through the Libreswan VM. In the
/etc/sysctl.conf
file, set the following values and apply the updates with
sudo sysctl -p
.
net.ipv4.ip_forward=1 net.ipv4.conf.all.accept_redirects = 0 net.ipv4.conf.all.send_redirects = 0 net.ipv4.conf.default.send_redirects = 0 net.ipv4.conf.eth0.send_redirects = 0 net.ipv4.conf.default.accept_redirects = 0 net.ipv4.conf.eth0.accept_redirects = 0
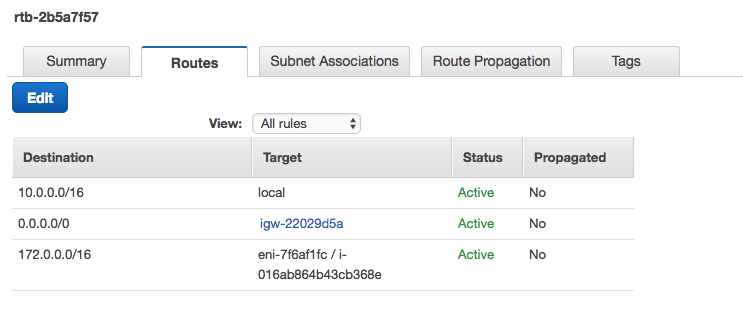
- Edit your AWS route table to add a rule that has the Oracle Cloud Infrastructure subnet CIDR (172.0.0.0/16) as the destination and the AWS Libreswan instance ID (i-016ab864b43cb368e) as the target.
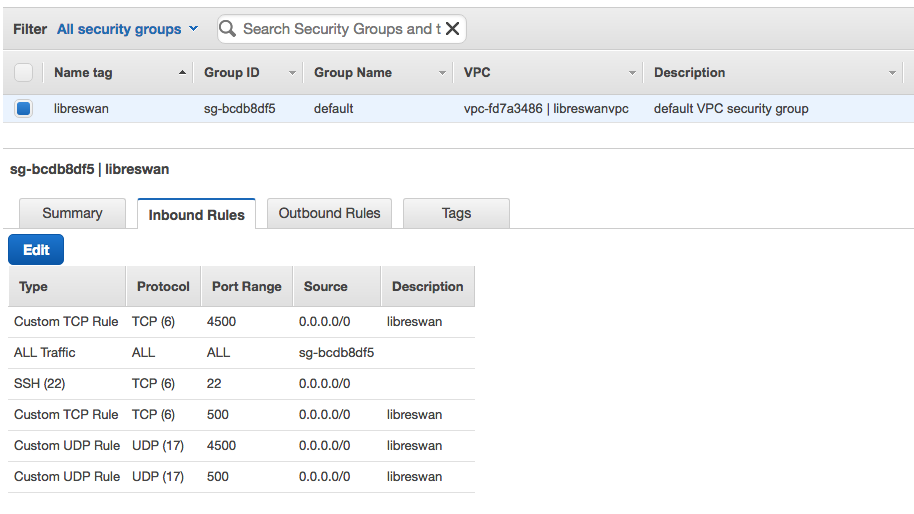
- Edit AWS security groups and network ACLs, and add TCP/UDP ports 4500 and 500 to allow Oracle Cloud Infrastructure DRG/CPE IPSec communication with the AWS Libreswan VM (the source option can be the Oracle Cloud Infrastructure public IP instead of 0.0.0.0/0).
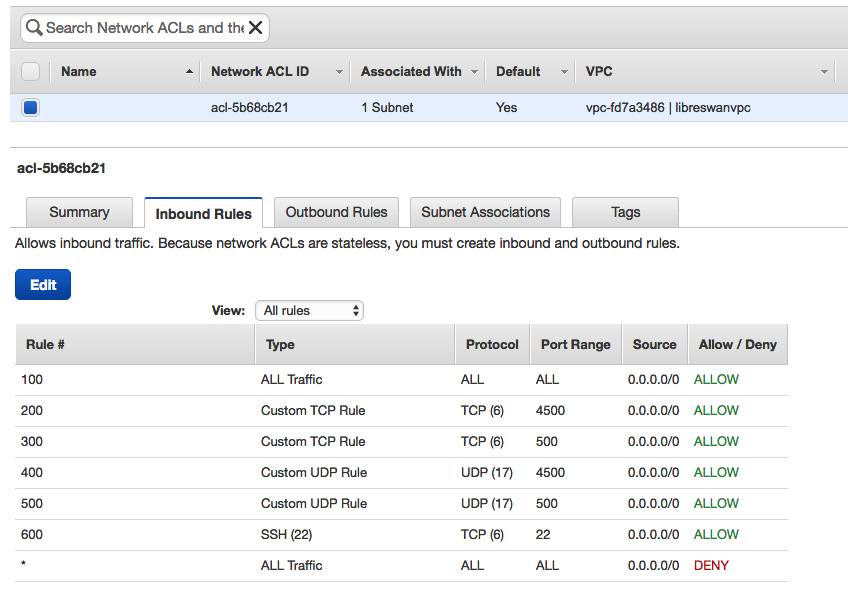
- Create the Libreswan IPSec configuration file.
$ sudo mv /etc/ipsec.conf /etc/ipsec.conf.bck $ sudo vi /etc/ipsec.conf and include the following config setup include /etc/ipsec.d/*.conf
Configure DRG and CPE on Oracle Cloud Infrastructure (Left Side)
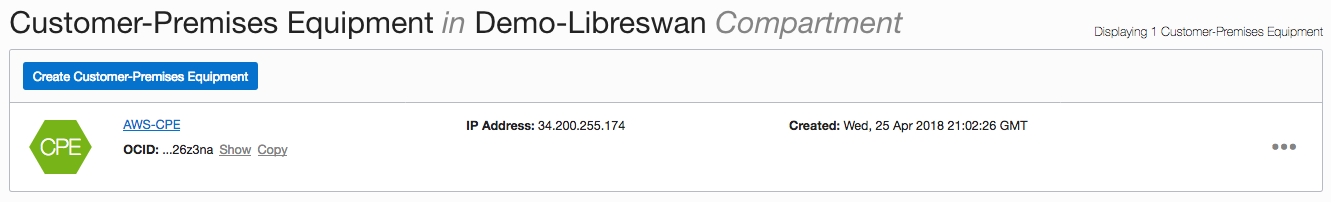
- Create a customer-premises equipment (CPE) that points to the Libreswan AWS instance public IP address (34.200.255.174).
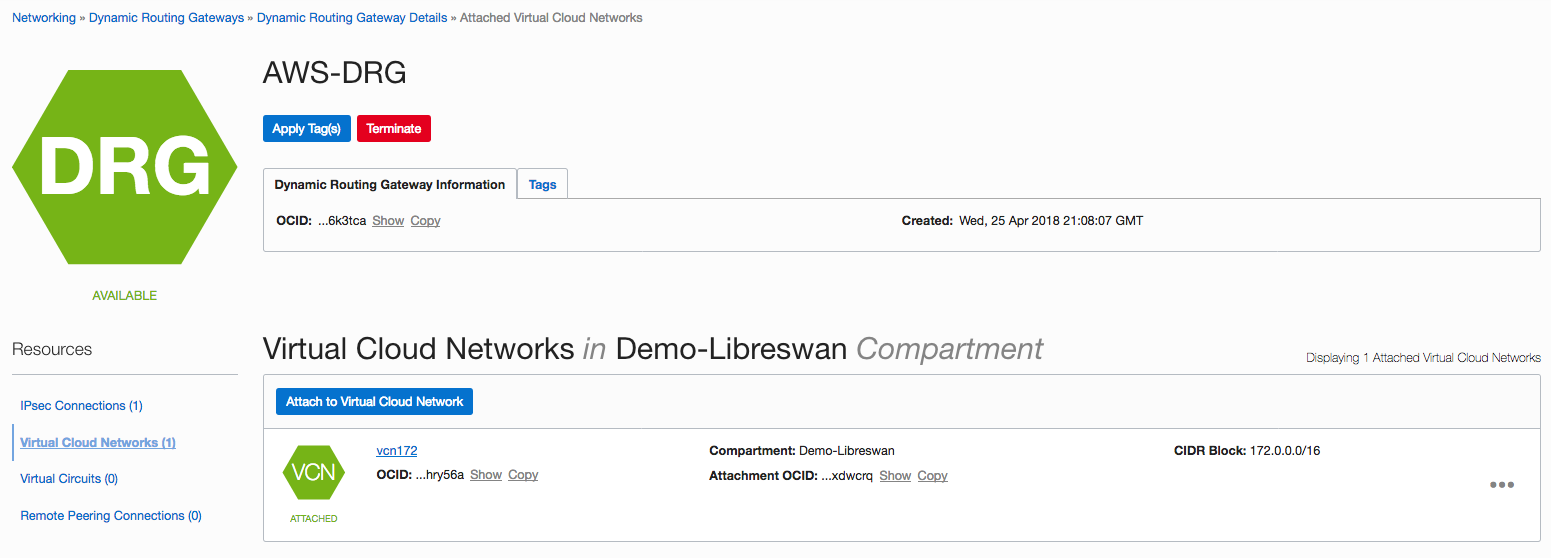
- Create a DRG and attach it to the Oracle Cloud Infrastructure local VCN (172.0.0.0/16).
- Create an IPSec connection and point it to the AWS VPC CIDR (10.0.0.0/16).
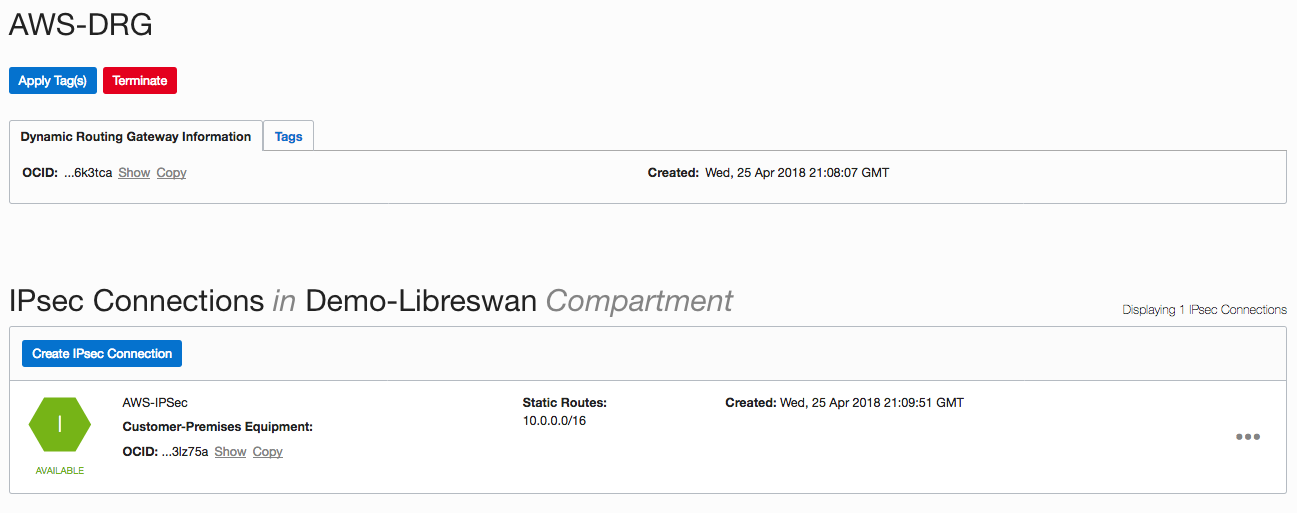
Initially the IPSec tunnel will be in the DOWN state (offline) because some additional configurations need to be done on the AWS Libreswan VM.
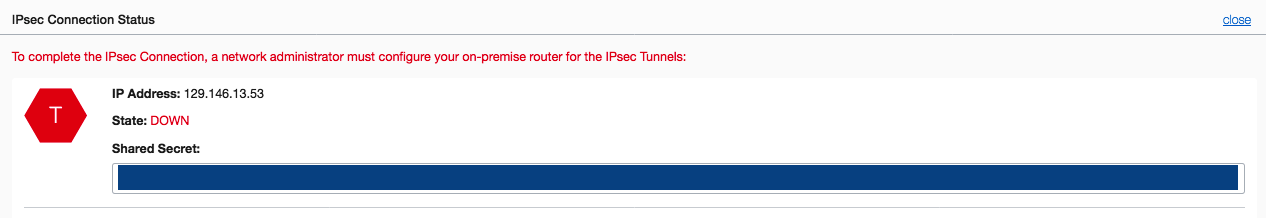
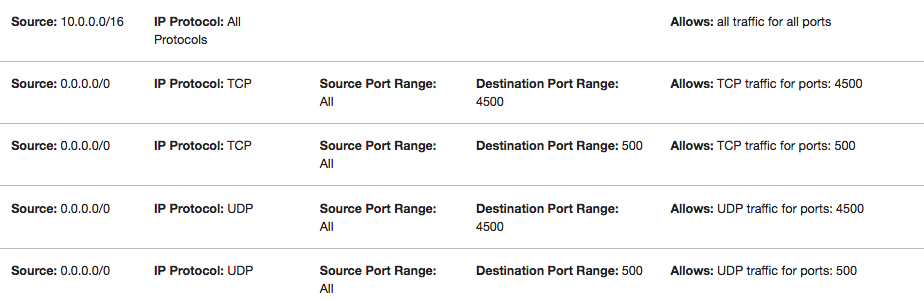
- Open ports 500 and 4500 (TCP/UDP) in the Oracle Cloud Infrastructure security list for 0.0.0.0/0, as you did with AWS security groups and networks ACLs. You can use the AWS Libreswan VM public IP address instead of 0.0.0.0/0 if it’s a persistent public IP. In addition to that, open ports/protocols for the AWS CIDR (10.0.0.0/16).
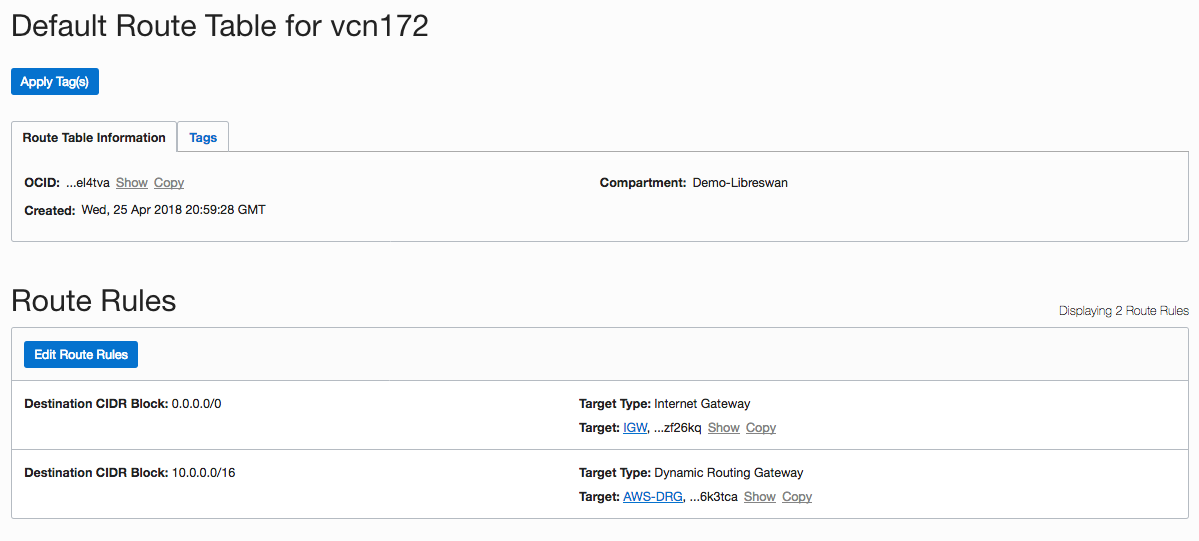
- Add a route rule to the AWS VPC network (10.0.0.0/16) using the DRG and CPE that you just created.
Finish the Third-Party Cloud Provider (AWS) Libreswan Configuration
- Connect through SSH to the AWS Libreswan instance and create the Libreswan IPSec connection file.
$ sudo vi /etc/ipsec.d/oci.conf and include the below options conn oci1 authby=secret auto=start pfs=yes salifetime=2500s leftid=129.146.13.53 #OCI DRG IPSec Public IP left=129.146.13.53 #OCI DRG IPSec Public IP leftsubnets=172.0.0.0/16 #OCI VCN CIDR right=10.0.0.10 #AWS Libreswan local VPC internal address rightid=34.200.255.174 #AWS Libreswan Public IP address rightsubnet=10.0.0.0/16 #AWS VPC CIDR vti-interface=${vti1} vti-routing=no mark=5/0xffffffff # Needs to be unique across all tunnels ikev2=no # To use IKEv2, change to ikev2=insist ike=aes_cbc256-sha2_384;modp1536 phase2alg=aes_gcm256;modp1536 encapsulation=yes ikelifetime=28800s NOTE:Review Access to other Clouds with Libreswan public documentation for current options. - For authentication, use the pre-shared key (PSK) option to create a secret file with a format similar to the following one:
$ sudo vi /etc/ipsec.secrets #OCI_DRG-Public-IP-IPSEC-Tunel1 AWS_OpenSWAN-PublicIP : PSK "DRG Secret Key" 129.146.13.53 34.200.255.174 : PSK "OCI DRG IPSec Secret Key"
- Run
sudo service ipsec restart
to start IPsec and
sudo ipsec auto –status |grep “===”
to verify that the tunnels were started correctly.
$ [centos@ip-10-0-0-10 ~]$ sudo ipsec auto --status |grep "===" 000 "oci1/1x0": 10.0.0.0/16===10.0.0.10<10.0.0.10>[34.200.255.174]...129.146.13.53<129.146.13.53>===172.0.0.0/16; erouted; eroute owner: #7 000 "v6neighbor-hole-in": ::/0===::1<::1>:58/34560...%any:58/34816===::/0; prospective erouted; eroute owner: #0 000 "v6neighbor-hole-out": ::/0===::1<::1>:58/34816...%any:58/34560===::/0; prospective erouted; eroute owner: #0
The configuration is complete, and in the Oracle Cloud Infrastructure Console, the IPSec tunnel should be the UP state.
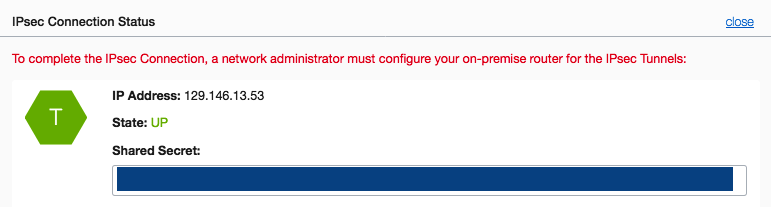
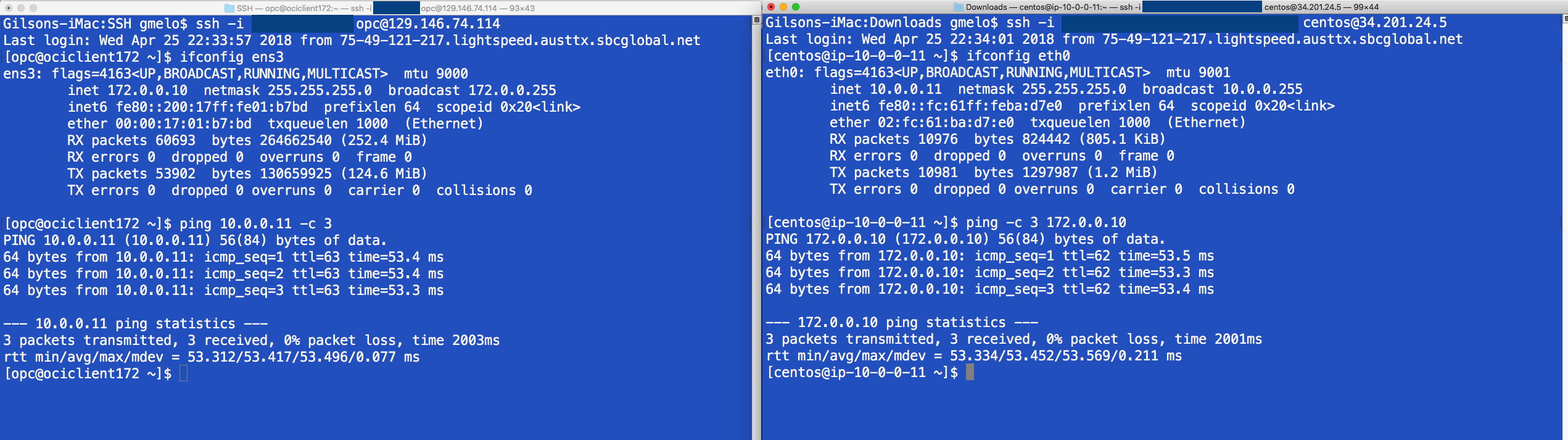
Quick IPSec Communication Test Between Oracle Cloud Infrastructure and AWS
Setup has been finalized so it’s time to validate the configuration and check if an OCI VM (Left Side) can communicate through an IPSec tunnel with an AWS VM (Right Side). One easy way to check the communication is through the ping command.
The below table explains both sides configuration.
| Left Side: Oracle Cloud Infrastructure VM |
Right Side – AWS VM |
| Public IP: 129.146.74.114 |
Public IP: 34.201.24.5 |
| VCN Local IP: 172.0.0.10 |
VPC Local IP: 10.0.0.11 |
and as the following image illustrates, both Cloud providers VMs can “talk” to each other.
Conclusion
This blog explained how to create a secure and encrypted site-to-site IPSec tunnel between Oracle and Amazon environments allowing the VMs to be able to communicate with each other through their private IP addresses as if they were in the same network segment.
