If you’re a typical Oracle Cloud Infrastructure customer, you may have resources in your virtual cloud network (VCN) that need to access the Oracle Cloud Infrastructure Object Storage service, which has publicly addressable endpoints. Until now, you could use either public subnets or a NAT instance, with an internet gateway in your VCN to access the service. However, you might not have wanted to use these options because of privacy, security, or operational concerns.
We are happy to announce the availability of the service gateway, which alleviates the preceding concerns by enabling the following functions:
- Private connectivity between your VCNs and Object Storage: You can add a service gateway to a VCN and use the VCN’s private address space to access Object Storage without exposing the instances to the public internet. You don’t need a public subnet, NAT instance, or internet gateway in your VCN.
- Enhanced security for your Object Storage buckets: You can limit access to Object Storage buckets from an authorized VCN or from a specific range of IP addresses within the subnet. You can add conditional references to VCN and IP addresses in IAM policies, which can only be satisfied when you initiate connections through a service gateway.
Accessing Object Storage Through a Service Gateway
You might have a private instance in your VCN that accesses the Object Storage bucket through a NAT instance and internet gateway. This section walks through that scenario and an example in which you enable the same private instance to access the same bucket privately and securely through a service gateway.
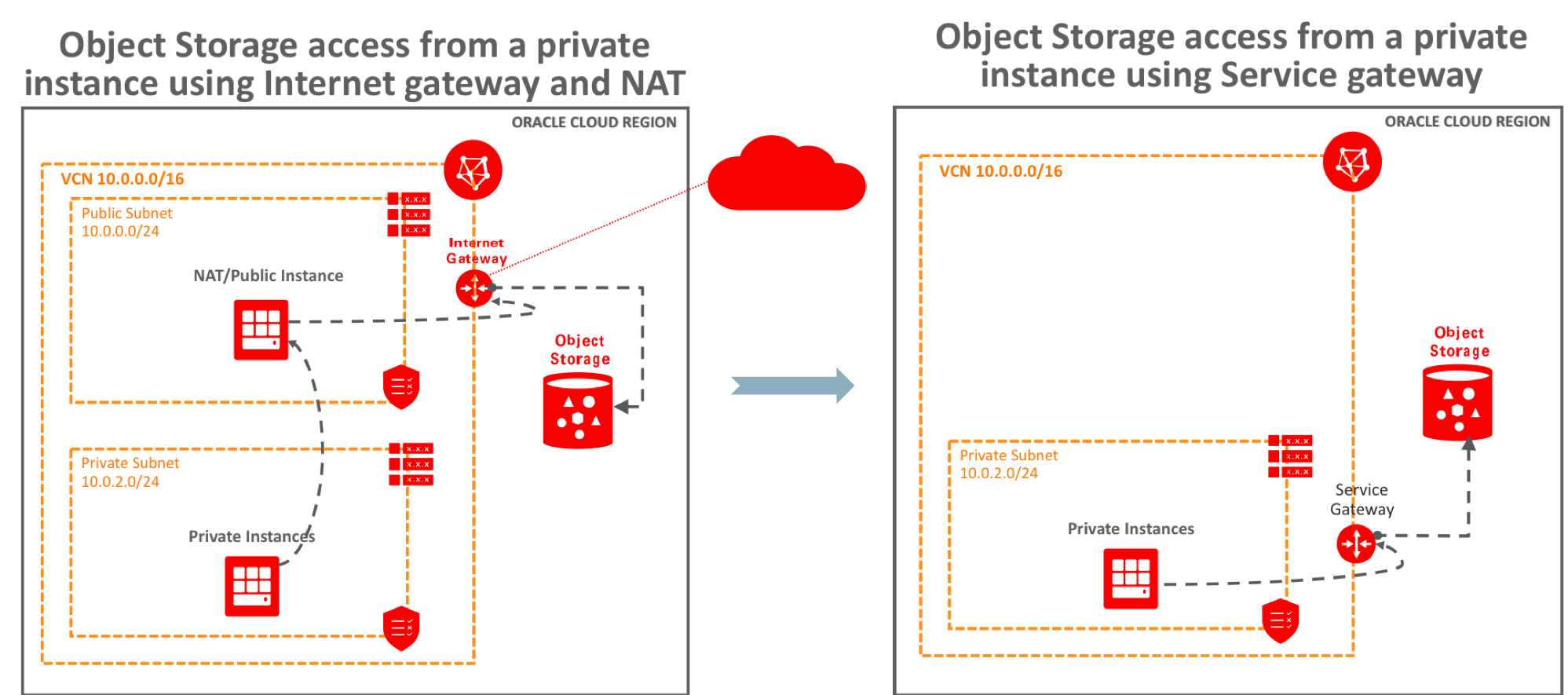
NAT Instance and Internet Gateway
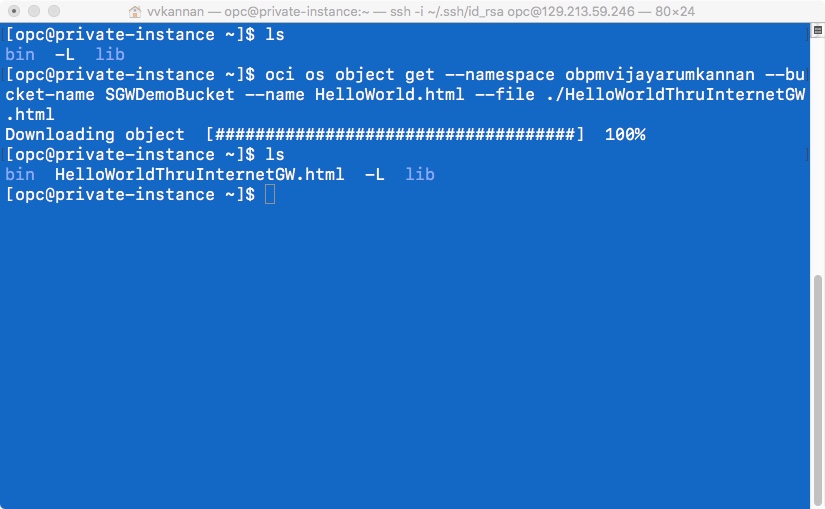
First consider a typical scenario in which private instances in the VCN access the Object Storage bucket through a NAT instance and internet gateway, as shown in the preceding figure.
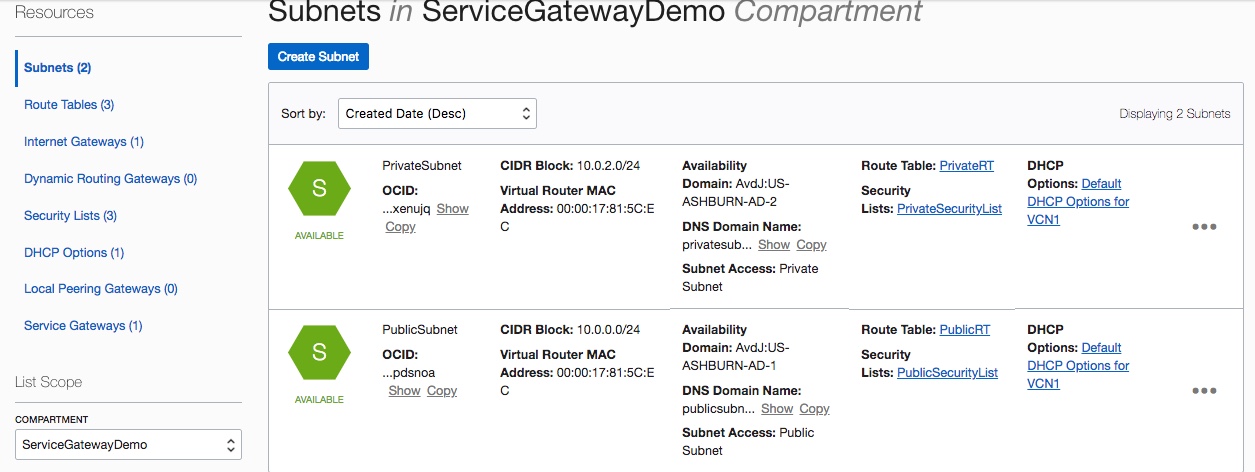
- Your VCN has one public subnet and private subnet with their associated route tables, security lists, and DHCP options created based on steps 1-3 described in this blog post.
- You also have an Object Storage bucket.
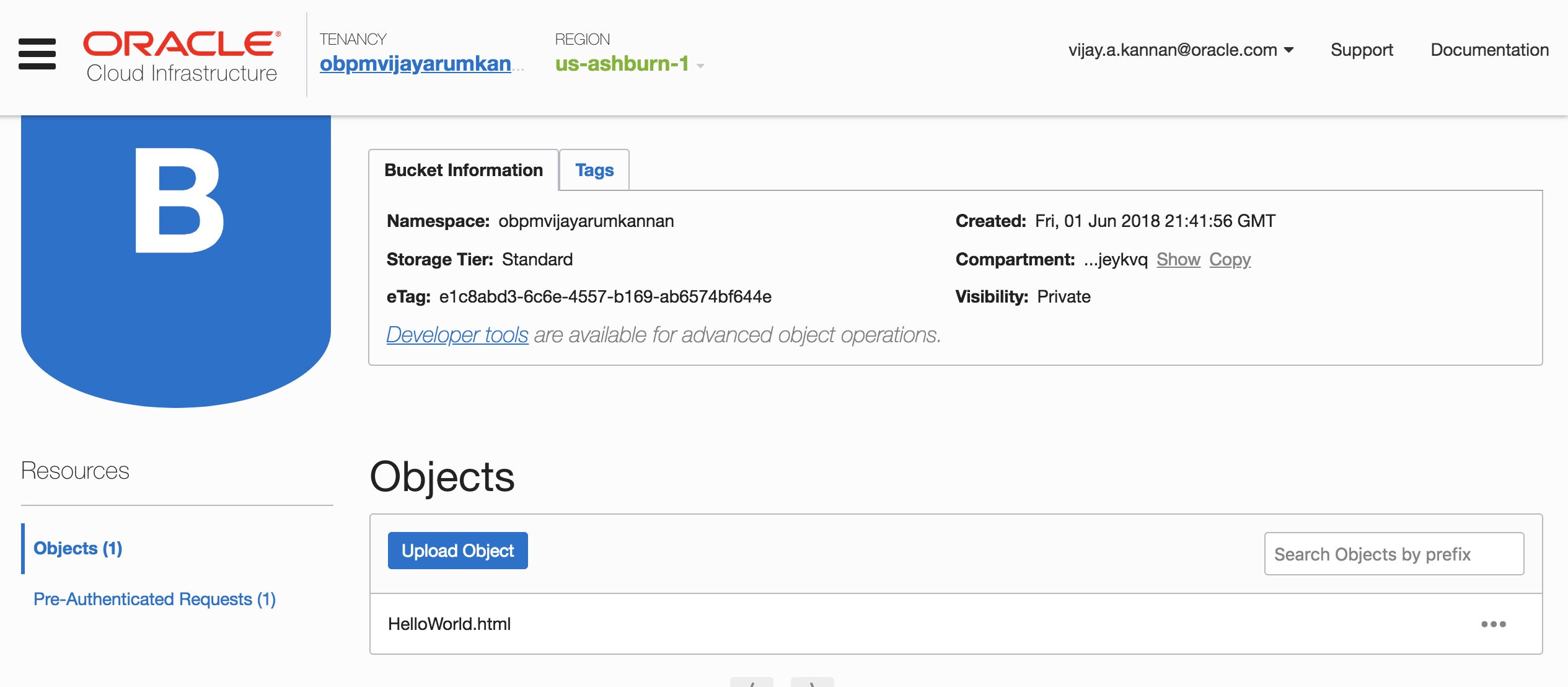
- You can use the Oracle Cloud Infrastructure Command Line Interface (CLI) to access the Object Storage bucket from the instances. The bucket is accessible from the instance in the private subnet through the NAT instance and the internet gateway.
Service Gateway
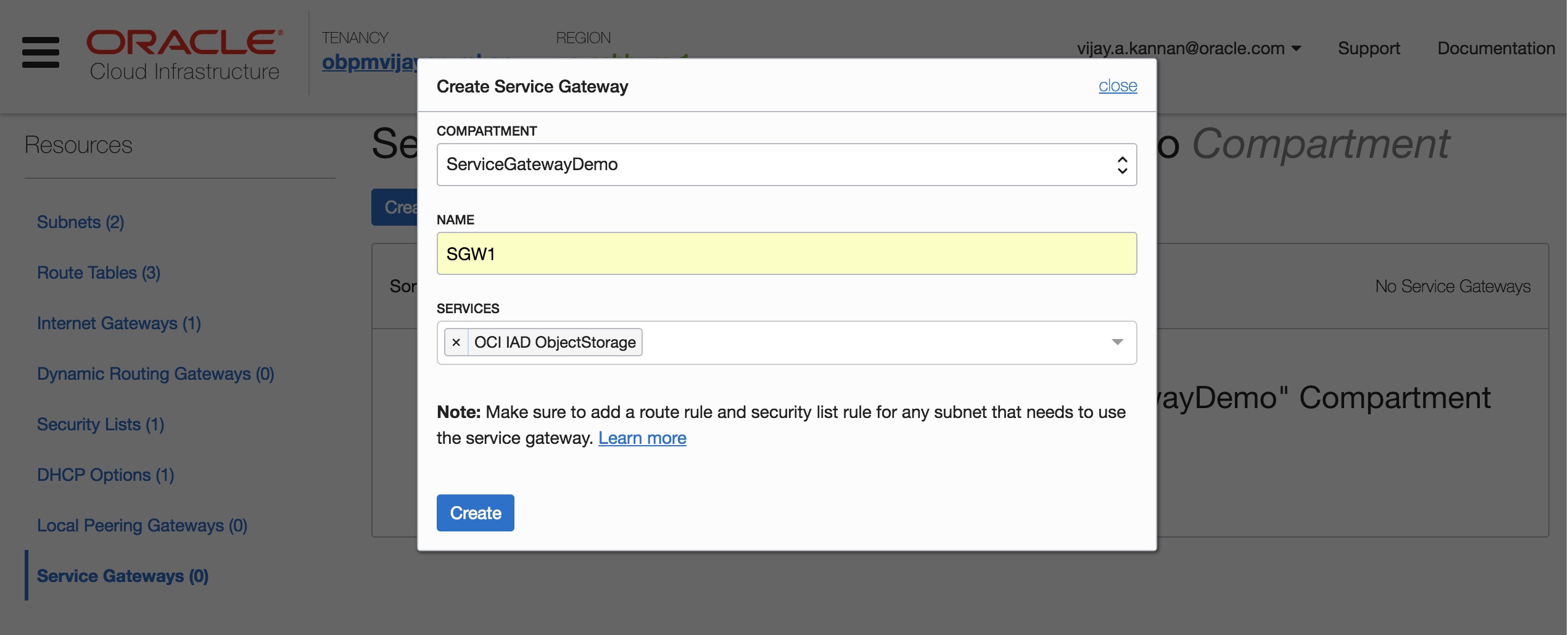
Now create a service gateway in the VCN and enable private connectivity between the private subnet and the Object Storage endpoint.
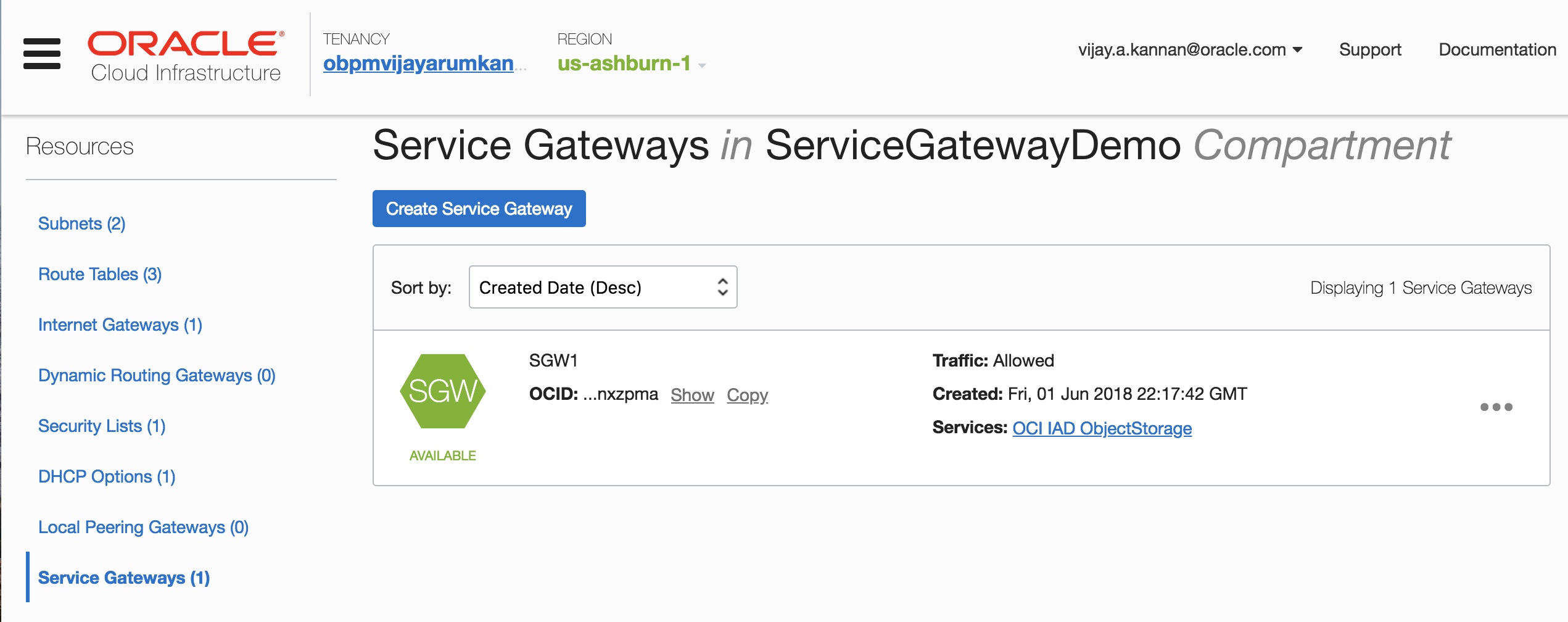
- You create a service gateway as a resource in the VCN just like you did with an internet gateway
- For traffic to be routed from a subnet in your VCN to the service gateway, add a route rule accordingly in the private subnet’s route table.
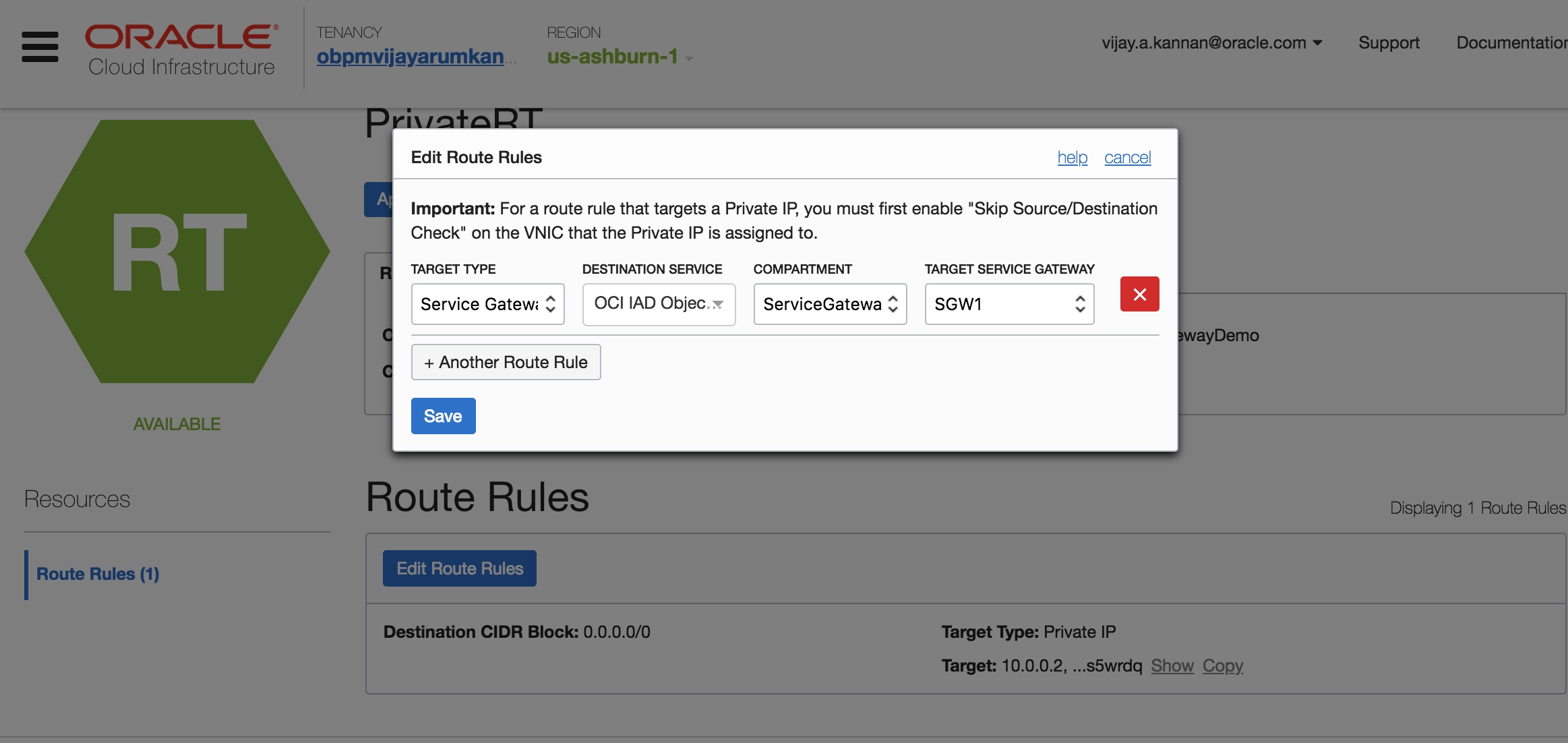
Note: With the launch of service gateway, we have now introduced Service CIDR labels, that can be used in place of a CIDR block in the route rules and/or security rules. This label maps to all IP addresses of the service within the regions. You don’t have to know the specific CIDR blocks for the service’s public endpoints, which could change over time. As you can see from the image above, you can now choose Service Gateway as the Target Type and provide the label of the OCI Object Storage Service.
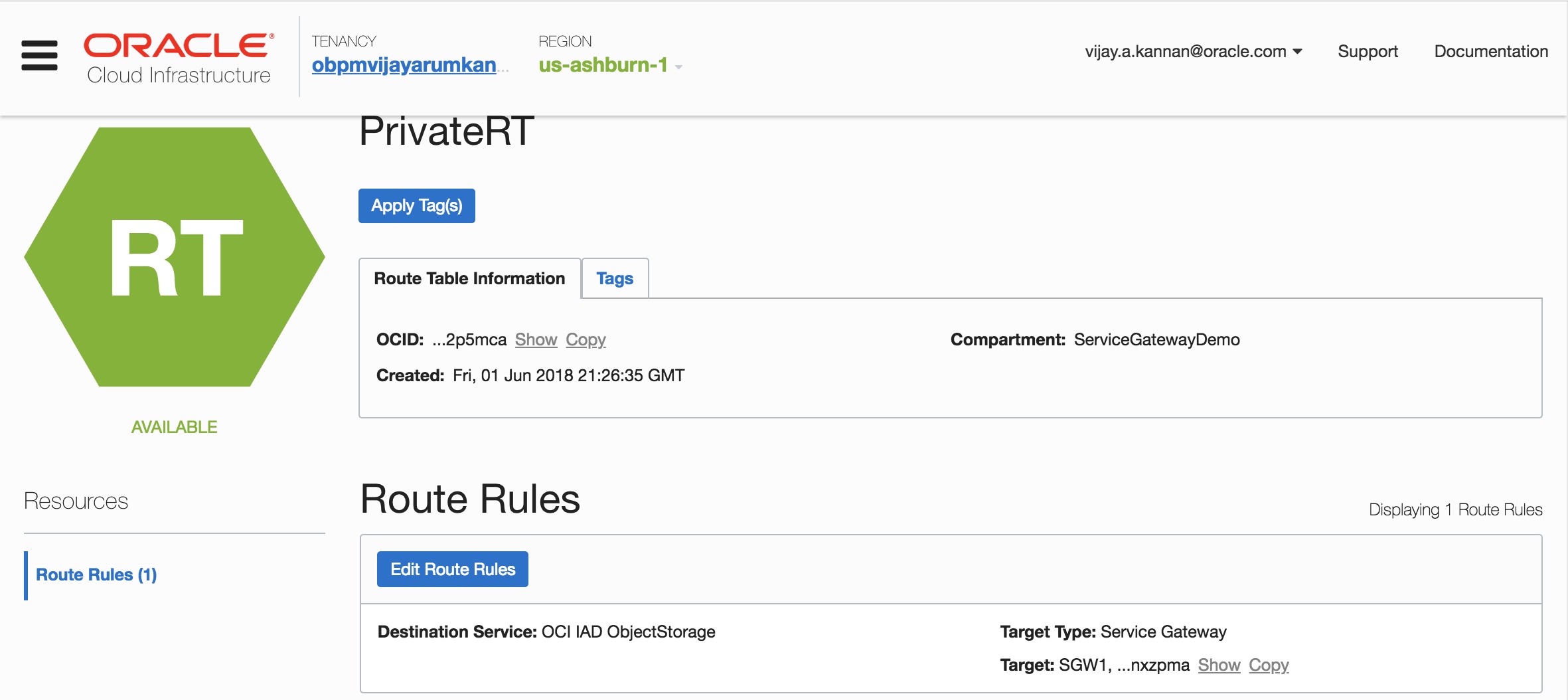
- You may choose to secure your private instance optionally by setting up egress security rules in the subnet’s security list for the traffic to the Object Storage service. As with route rules, you can specify the Object Storage service as the destination service in the security rule.
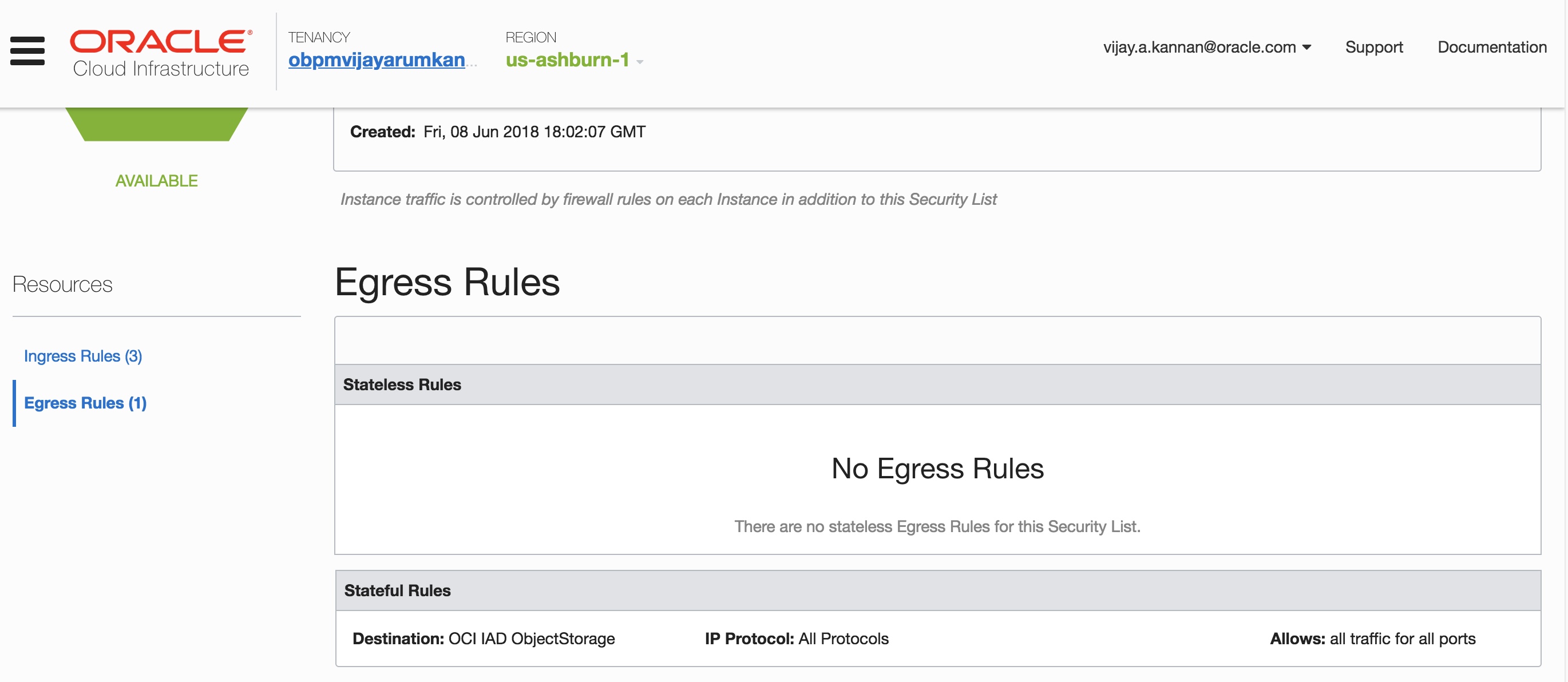
- You have now removed the dependency on the NAT instance and internet gateway for Object Storage access. The Object Storage bucket is now accessible from the instance in the private subnet through the service gateway.
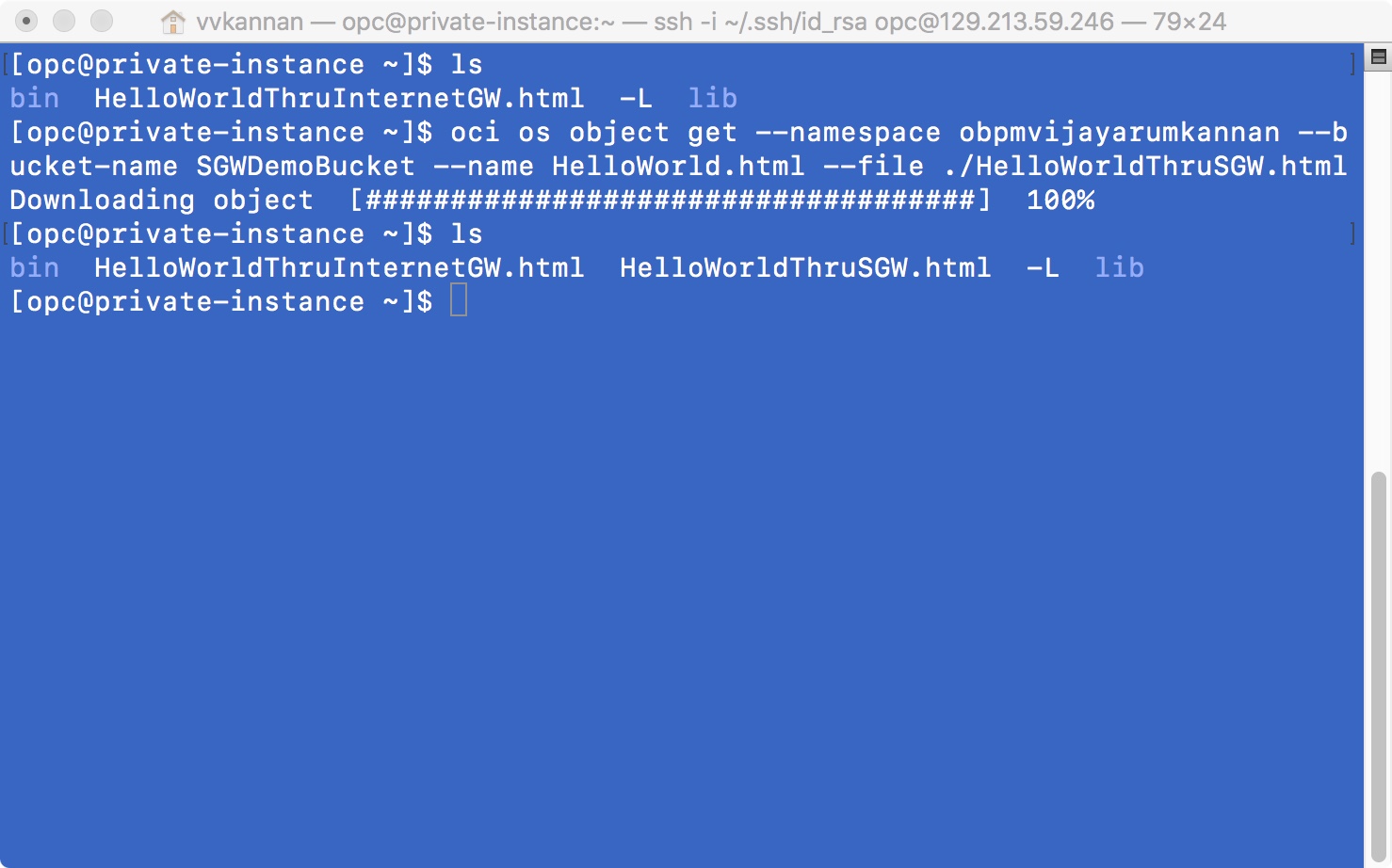
Voila! You have now successfully introduced a service gateway to your VCN to establish private connectivity between the private instance and an Object Storage endpoint.
Note: If your private instances need internet access for software updates or other functions, you may use the internet gateway and NAT instance in the VCN. In this case, you will need one route rule for the Object storage CIDR blocks through the service gateway and an additional default route rule in the private subnet route tables that direct all other traffic through NAT instance as shown below:
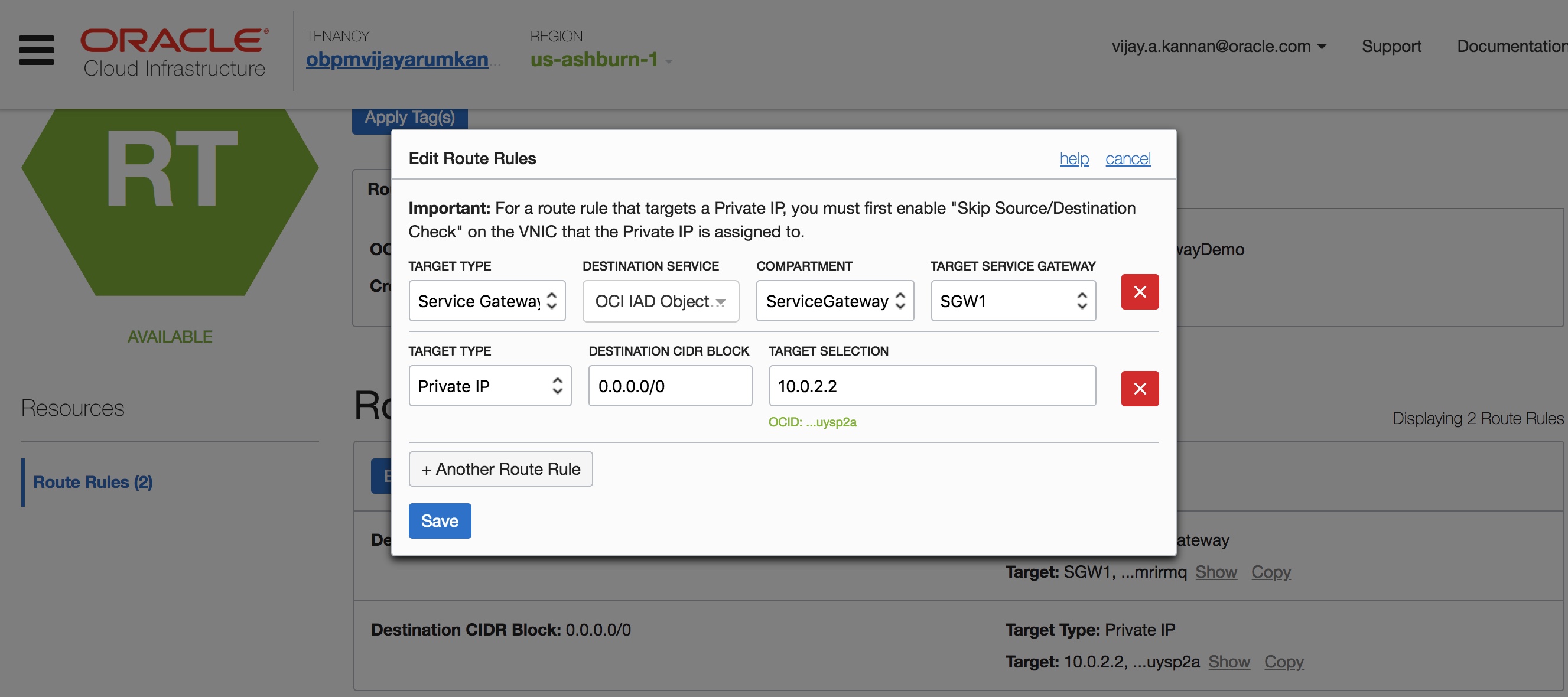
Let’s take a minute to look at other features of the service gateway:
- You can block or allow traffic through the service gateway. Blocking the service gateway prevents all traffic regardless of any existing route rules or security lists in your VCN. This flexibility provides administrative-level control at a single point in the network without having to update security or route rules at different subnets.
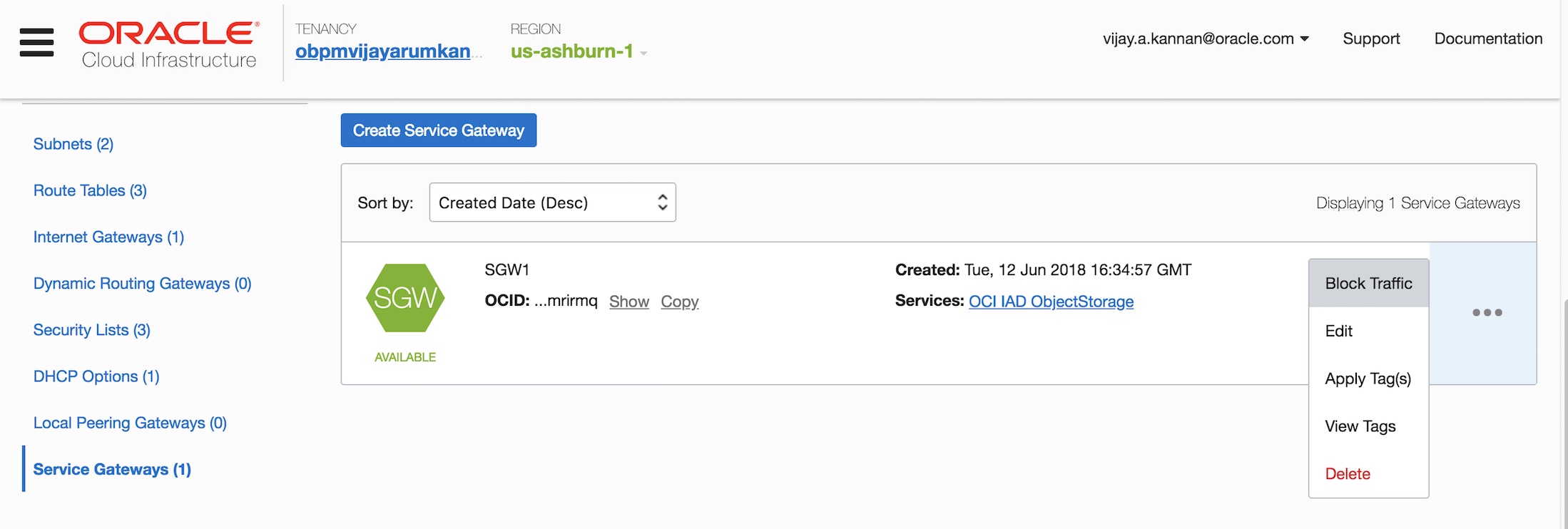
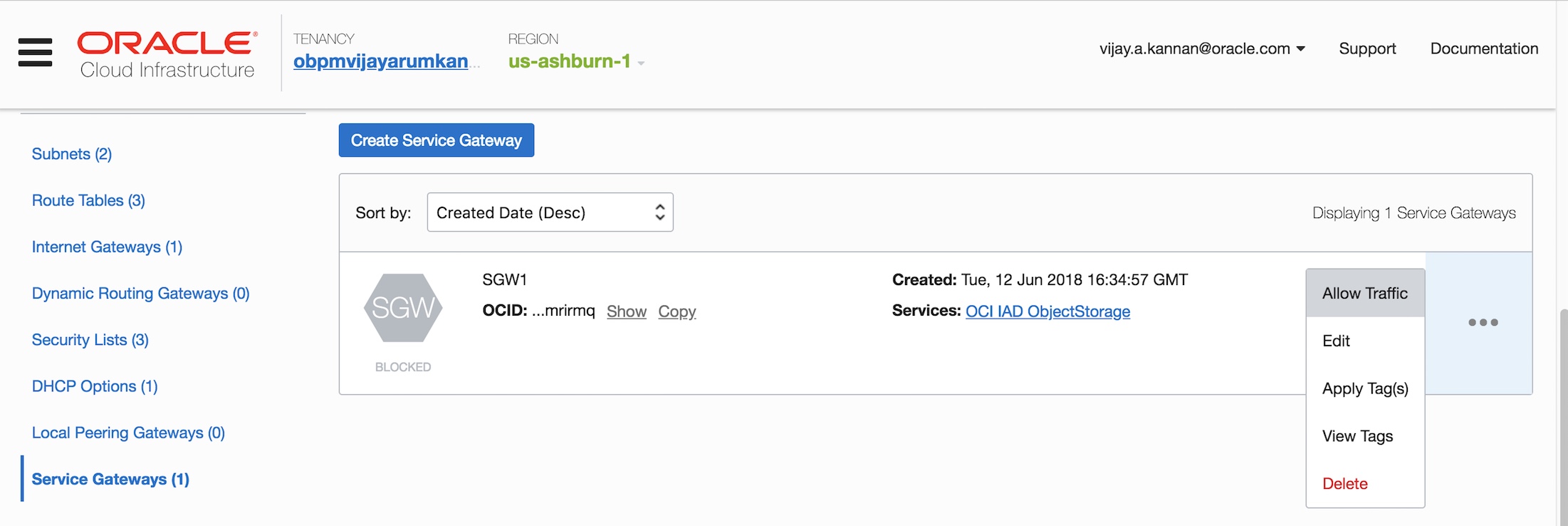
- You can also lock access to an Object Storage bucket to specific VCNs by using IAM policies for providing enhanced security for your objects. Following is a sample IAM policy that locks down an Object Storage bucket to be accessible from a specific VCN.
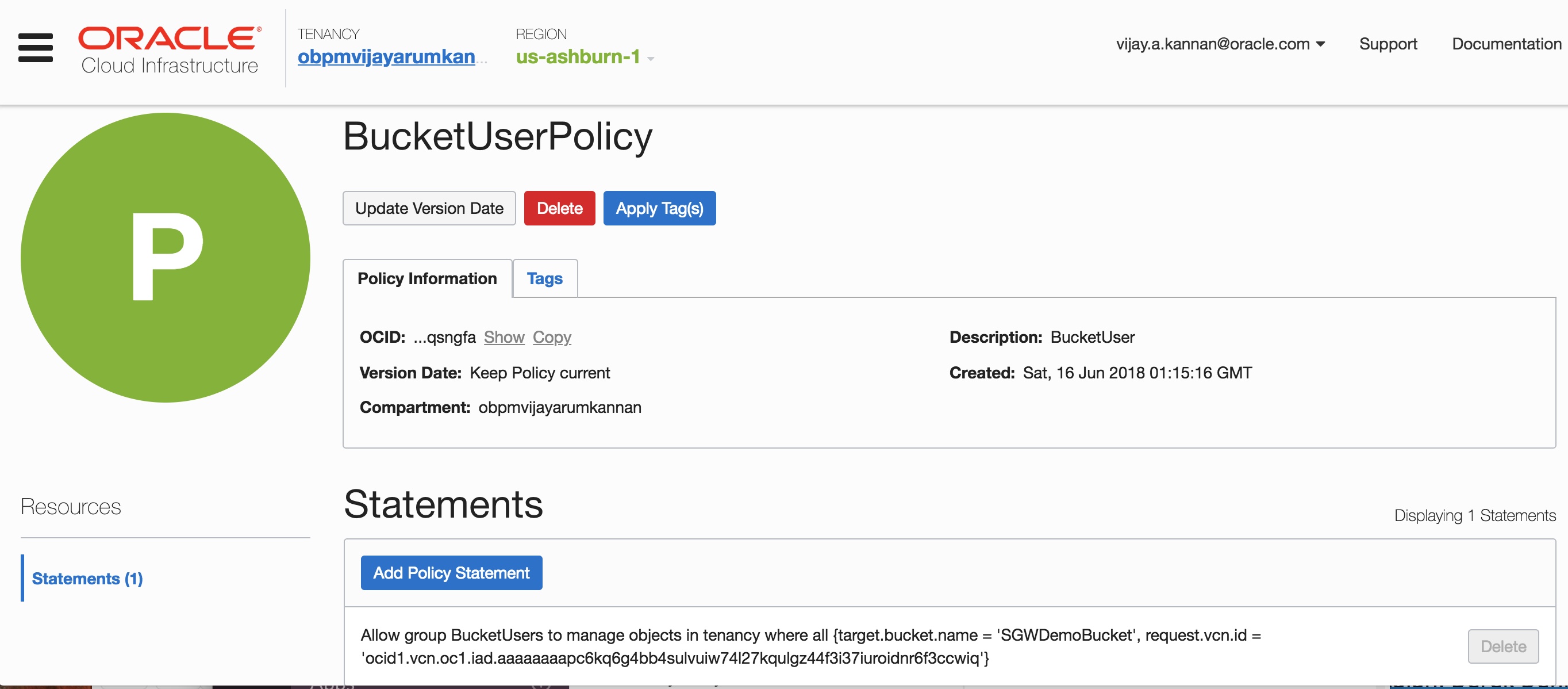
We recommend that you use the service gateway for all your Object Storage access needs. You can find more information about the service gateway in the Networking documentation.
Thank you for reading this post. Your feedback and recommendations for the post are most welcome.
Vijay Arumugam Kannan
Principal Product Manager
Oracle Cloud Infrastructure, Networking
