The Oracle Cloud Infrastructure Identity and Access Management (IAM) service lets you control who has access to your cloud resources. You can control what type of access a group of users has and to which specific resources. The service enables you to enforce the security principle of least privilege by default. New users are not allowed to perform any actions on any resources until they are granted appropriate permissions.
With the IAM service, you can leverage a single model for authentication and authorization across all Oracle Cloud Infrastructure services. IAM makes it easy to manage access for organizations of all sizes, from one person working on a single project to large companies with many groups working on many projects at the same time, all within a single account.
I recently published a white paper with a list of best practices for the IAM service on Oracle Cloud Infrastructure. In this blog post, I want to highlight a couple of those best practices.
Compartment and Group Policy Design Strategy
Compartments are the primary building blocks that you use to organize and isolate resources, which makes it easier to manage and secure access to them. Compartment provides flexibility and granularity to separate resources for the purposes of measuring usage and billing, access and isolation. It is a very unique and useful feature of OCI to meet customers’ security and governance requirements.
When you start working with Oracle Cloud Infrastructure, you must carefully consider how you want to use compartments to organize and isolate your cloud resources. It is important to consider the compartment design for your organization before you implement anything.
Please consider the following aspects when you start working with compartments:
- When you create a resource (for example, a compute instance, block storage volume, VCN, or subnet), you must place it in a compartment.
- Compartments are logical, not physical, so related resource components can be placed in different compartments. For example, your cloud network subnets with access to an internet gateway can be secured in a separate compartment from other subnets in the same cloud network.
- After a resource is created, it can’t be moved to another compartment.
- When you write a policy rule to grant a group of users access to a resource, specify the compartment that you want to apply the access rule to. If you distribute resources across compartments, you must provide the appropriate permissions for each compartment for users who need access to those resources.
- Compartments can’t be deleted, so do not create multiple “test” compartments with the intent to delete them later.
- When planning for compartments, consider how you want aggregate usage and auditing data, which might be a consideration for your company in the future.
Your compartment design depends on your use cases and how you want to organize and isolate your resources.
The following scenario illustrates how to design your compartments and define related policies.
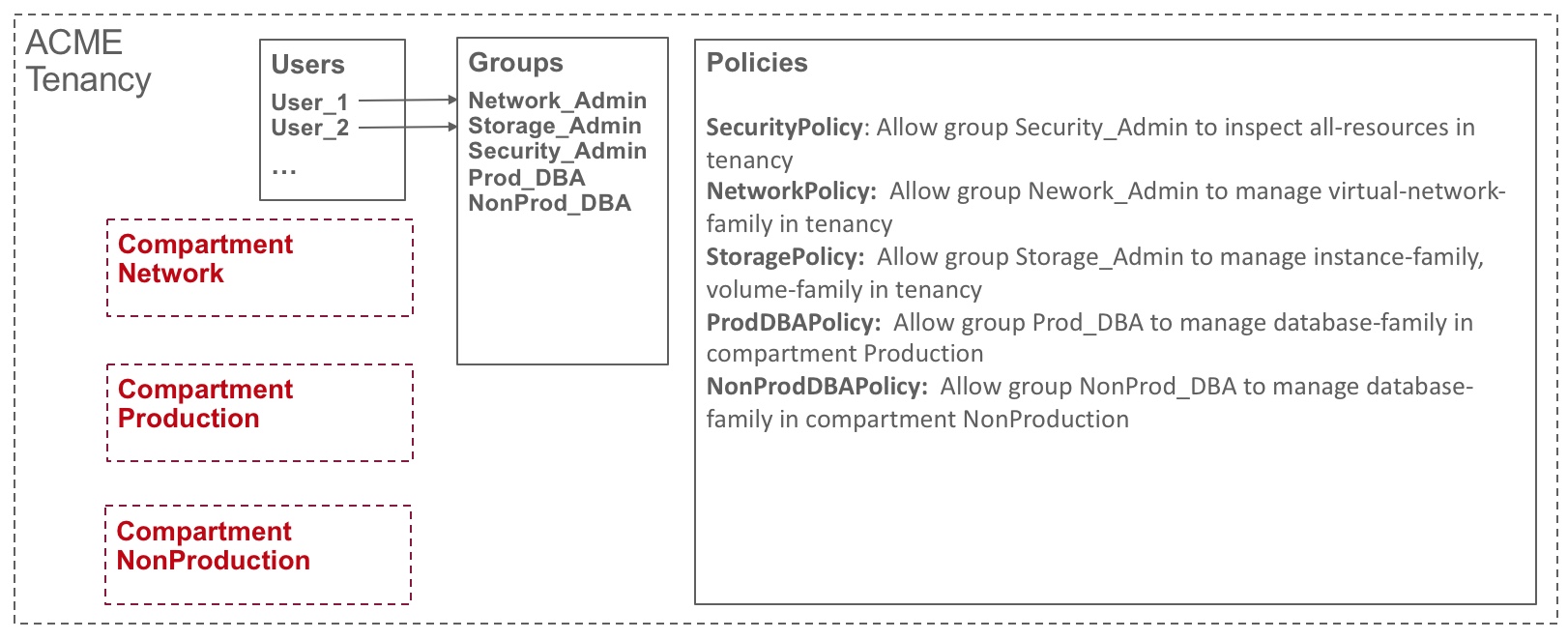
Company ACME wants to have three dedicated environments for their workload management. One environment is dedicated to network management and all the network resources are managed in this environment. Another environment is for production workloads, and the last environment is for non-production workloads. ACME has multiple types of administrators: DBAs, network admins, storage admins, and security admins. Each DBA manages databases of production and non-production environments respectively. Network admins, storage admins, and security admins need to access and manage corresponding network, storage, and security-related resources in the tenancy.
To accommodate these needs, create three compartments to align with ACME’s three different environments. For instance, we define “network”, “production” and “non-production” compartments. Then, define groups that map to each type of administrator. For instance, “Network_Admin” group is dedicated for network administrator who has full rights to manage all network related resources. Finally, define policies to control who can access which resources.
The following diagram illustrates a possible compartment and policy design for this scenario:
Federation
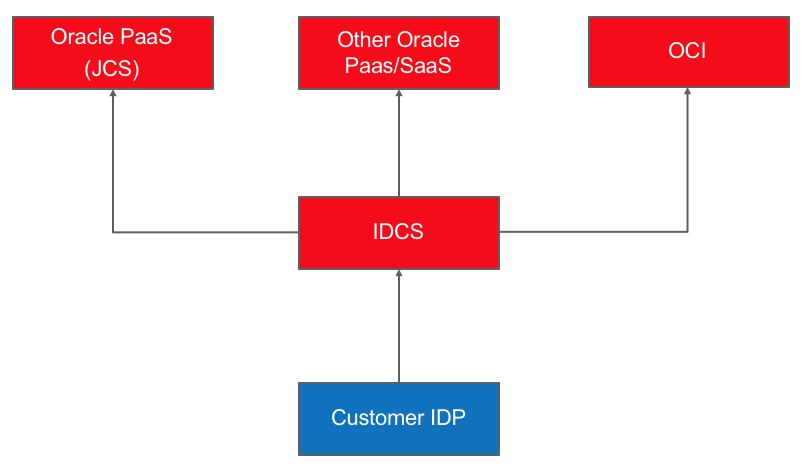
Oracle Cloud Infrastructure IAM supports federation with Oracle Identity Cloud Service (IDCS), Microsoft Active Directory Federation Services (ADFS), and other Security Assertion Markup Language (SAML) 2.0 compliant IDPs. When you sign up for Oracle Cloud Infrastructure, your tenant administrator account is automatically federated with Oracle Identity Cloud Service. Federating Oracle Cloud Infrastructure with Oracle Identity Cloud Service automatically allows you to have a seamless connection between services without having to create a separate username and password for each one.
We recommend that customers federate their favorite IDP with IDCS which will automatically provide federation for all Oracle cloud offerings, including Oracle Cloud Infrastructure.
Check out our white paper for more best practices on how to securely manage and control access to your cloud resources. You can also learn more about security best practices for Oracle Cloud Infrastructure’s Identity and Access Management (IAM) service. Please take a look at these resources and share your feedback.