Reliable, high-performance infrastructures are important to keep your services up and running, and automating applications failover is a crucial to avoid losing business or impacting end-user experience.
This blog explains how to create a highly availabe environment for your Oracle Cloud Infrastructure Virtual Private Network (VPN) compute instances to eliminate single points of failure. In the event that an instance fails, the VPN server will automatically be started on a healthy instance and the user VPN client will be immediately reconnected to minimize the downtime experience.
Getting Started
First, let’s explore the components that will be used and that you need to be familiar with. These are the main requirements needed to enable your VPN service to failover automatically on Oracle Cloud Infrastructure:
- Pritunl Enterprise VPN Cluster
- MongoDB single instance. Feel free to use another database application if you’re not familiar with MongoDB and make sure it works with Pritunl first.
- Oracle Linux 7.x Instances will be used to host this environment
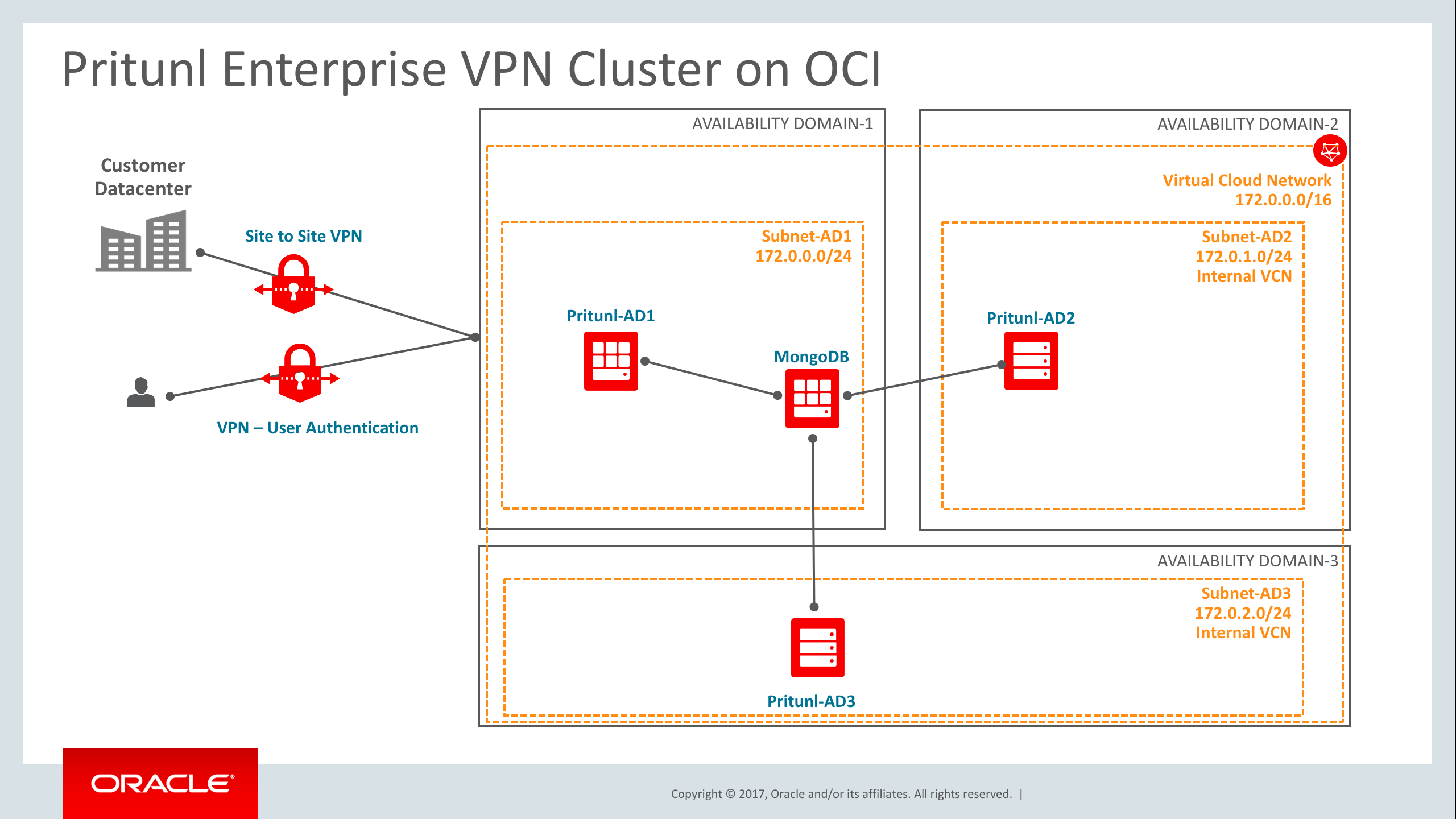
Architecture
Configuration Process
Using Pritunl on Oracle Cloud Infrastructure to automate the VPN Server failover and client reconnection is very simple:
1- Provision four Oracle Cloud Linux Instances. One node will host MongoDB so choose the appropriate Instance shape based on the workload. The remaining instances will be used for the Pritunl VPN servers – one in each of the three Availability Domains in the region, for fault tolerance.
2- Configure SElinux properly on all servers (or disable it) and open the appropriate ports in the local linux firewall like mongodb port, https, etc.
3- Enable only the required ports for the internal network using the Oracle Cloud Infrastructure Dashboard Security List Option for the above services as well. Below is an example for MongoDB port.
| Source: 172.0.0.0/16 |
4- Make sure that ports 443 (HTTPS) and 27017 (mongoDB) are enabled for 0.0.0.0 (internet) communication.
5- One single MongoDB is going to be used in this configuration but you can configure a MongoDB Cluster for additional security if needed. Configure the MongoDB instance as shown below for Oracle Linux 7.x/CentOS 7.x. Additional Linux operating systems can be used and there are some configuration examples here.
| sudo tee -a /etc/yum.repos.d/mongodb-org-3.4.repo << EOF [mongodb-org-3.4] sudo yum -y install epel-release gpg –keyserver hkp://keyserver.ubuntu.com –recv-keys 7568D9BB55FF9E5287D586017AE645C0CF8E292A |
6- Install the Pritunl application on the VPN instances (3 instances)
| sudo tee -a /etc/yum.repos.d/pritunl.repo << EOF [pritunl] sudo yum -y install epel-release |
7- Run the commands below to increase the open file limit on the server. This will prevent connections issues on servers with high load. This should also be done on the MongoDB server.
| sudo sh -c ‘echo “* hard nofile 64000” >> /etc/security/limits.conf’ sudo sh -c ‘echo “* soft nofile 64000” >> /etc/security/limits.conf’ sudo sh -c ‘echo “root hard nofile 64000” >> /etc/security/limits.conf’ sudo sh -c ‘echo “root soft nofile 64000” >> /etc/security/limits.conf’ |
8- Change the MongoDB bindIP listener in /etc/mongod.conf from 127.0.0.1 to the internal IP address associated with the OS NIC (i.e.; 172.0.0.55). Restart Mongodb (i.e.; sudo systemctl restart mongod)
9- Create a user for Pritunl by first connecting with the mongo cli. Once connected switch to the pritunl database and run the create user command. Change the PASSWORD below to a secure random password.
| run mongo CLI to create an user called pritunl along with a password. Change “PASSWORD” to any password you want to use. mongo mongodb://172.0.0.55:27017 |
10- Identify the VPN Instance’s public IP address, open a browser and type https://publicIP-VPNServer1. When Pritunl starts for the first time a database setup prompt will be shown on the web server running on port 443 and the database setup will prompt for a setup key and MongoDB URL. To get the setup key, ssh on to the server and run the command “pritunl setup-key” and this will return the setup key. By default the MongoDB URL will be filled with the uri for the localhost MongoDB server so make sure to change the default URL to “mongodb://pritunl:PASSWORD@MONGODB_INTERNAL_IP:27017/pritunl” as the following example for a MongoDB instance with a local IP 172.0.0.55, using username “pritunl” and password “PASSWORD” (default username and password are “pritunl”).
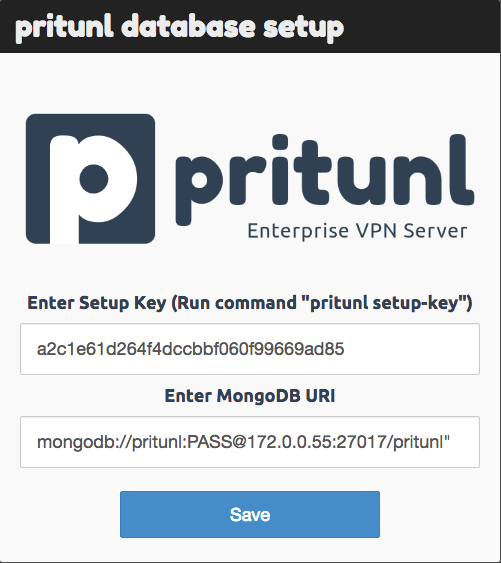
Repeat this process on all additional VPN instances in your environment.
11- Configure Pritunl using the main dashboard.
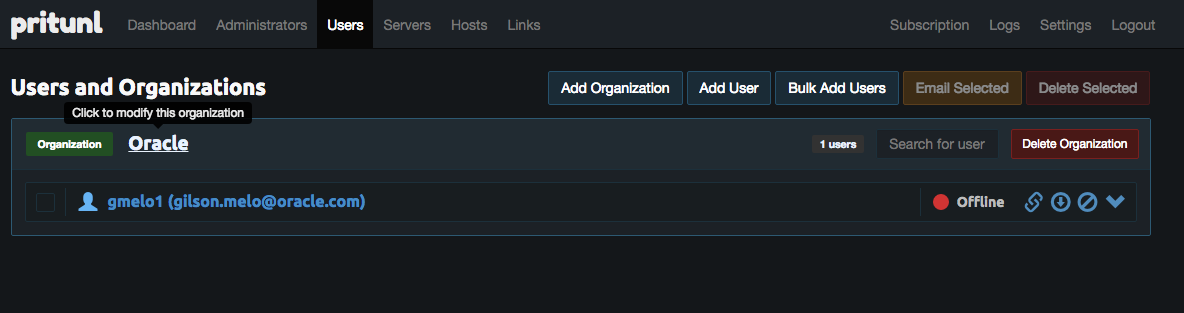
11a- Create an Organization (i.e.; Oracle) and users
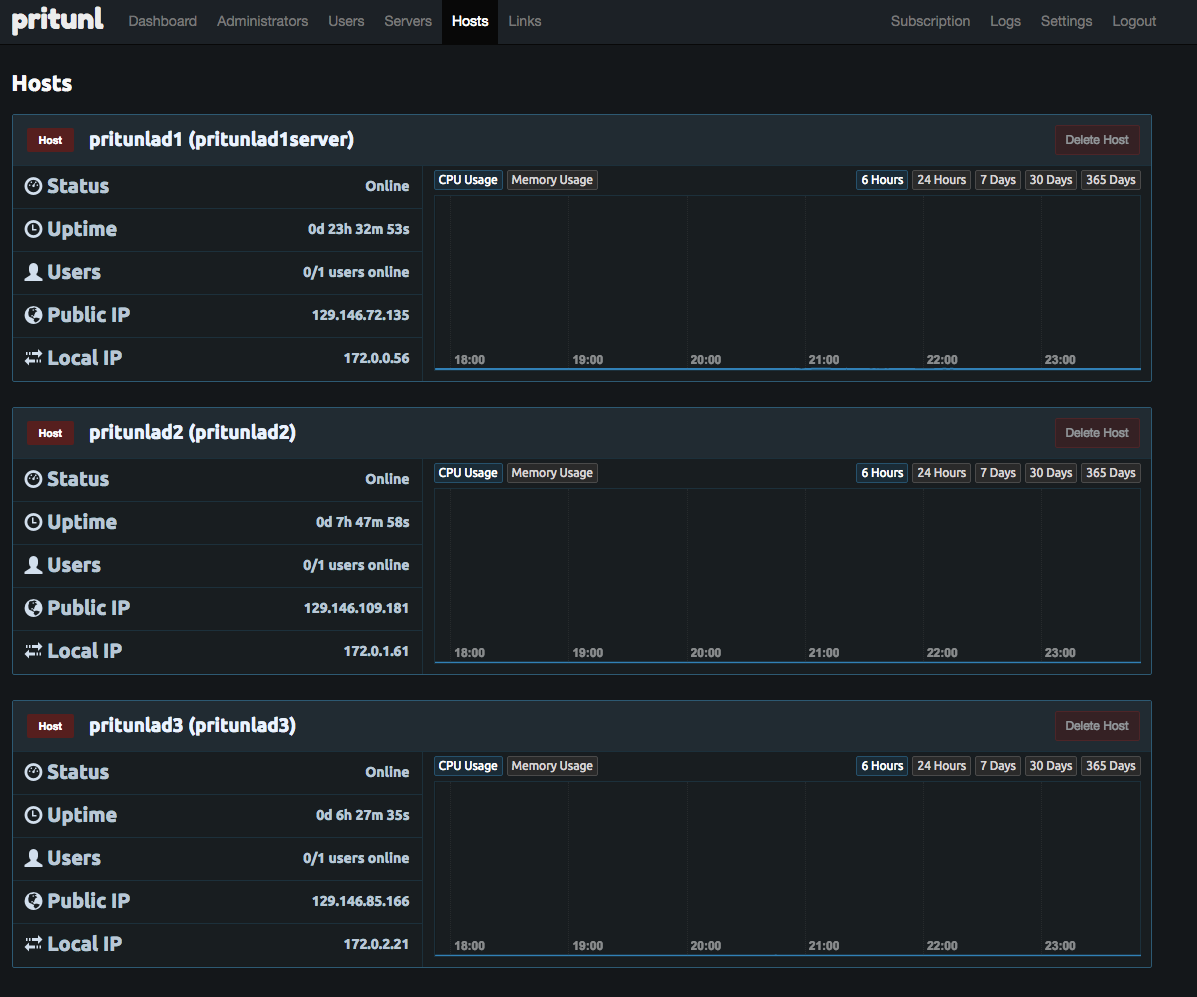
11b- Check the Hosts tab to make sure all the VPN instances are there and update the names if needed
11c- Create a new Server and pay attention to the protocol, port and Virtual Network subnet that you are using.
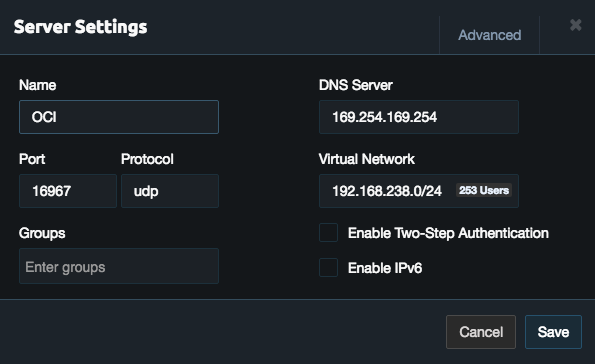
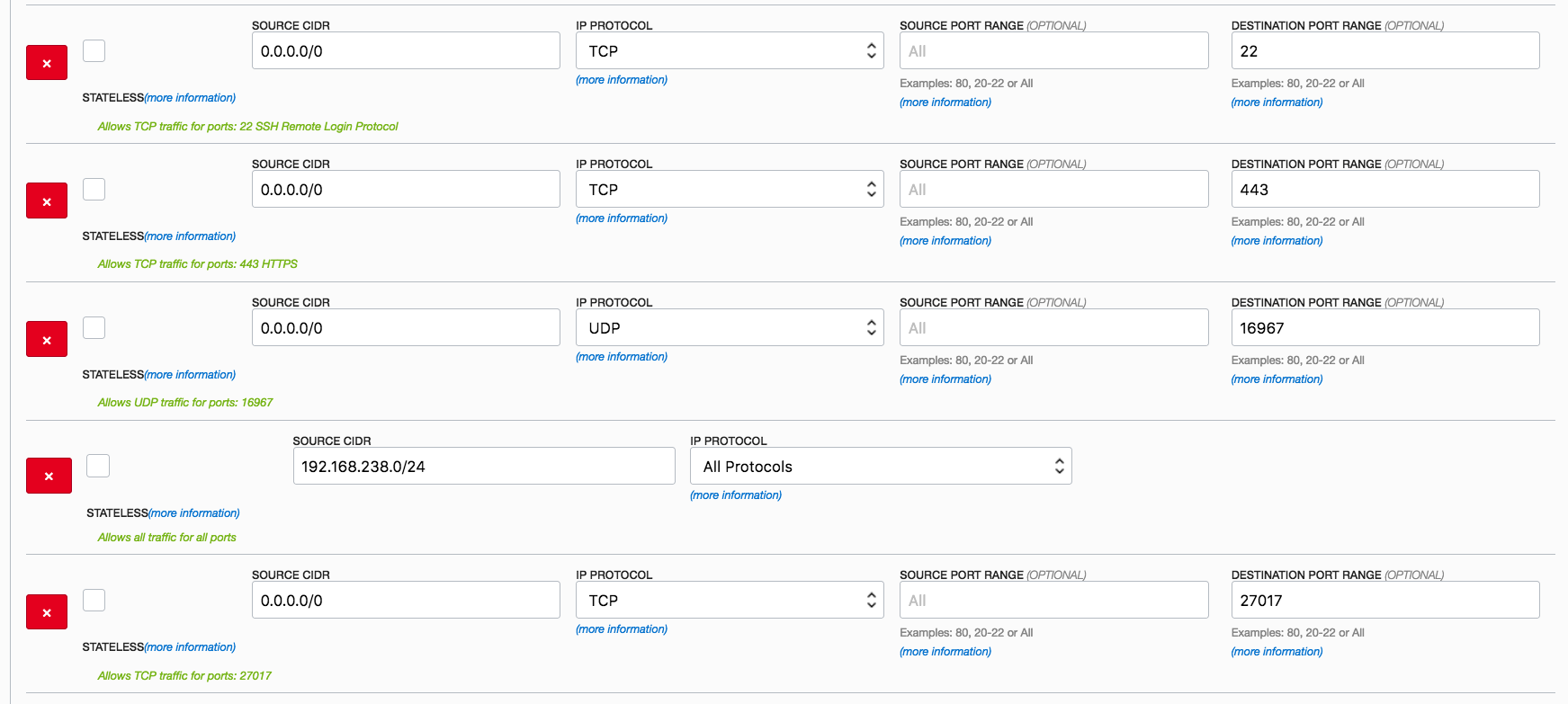
11d- Make sure you enable the above port, protocol and network using Oracle Cloud Infrastructure Dashboard
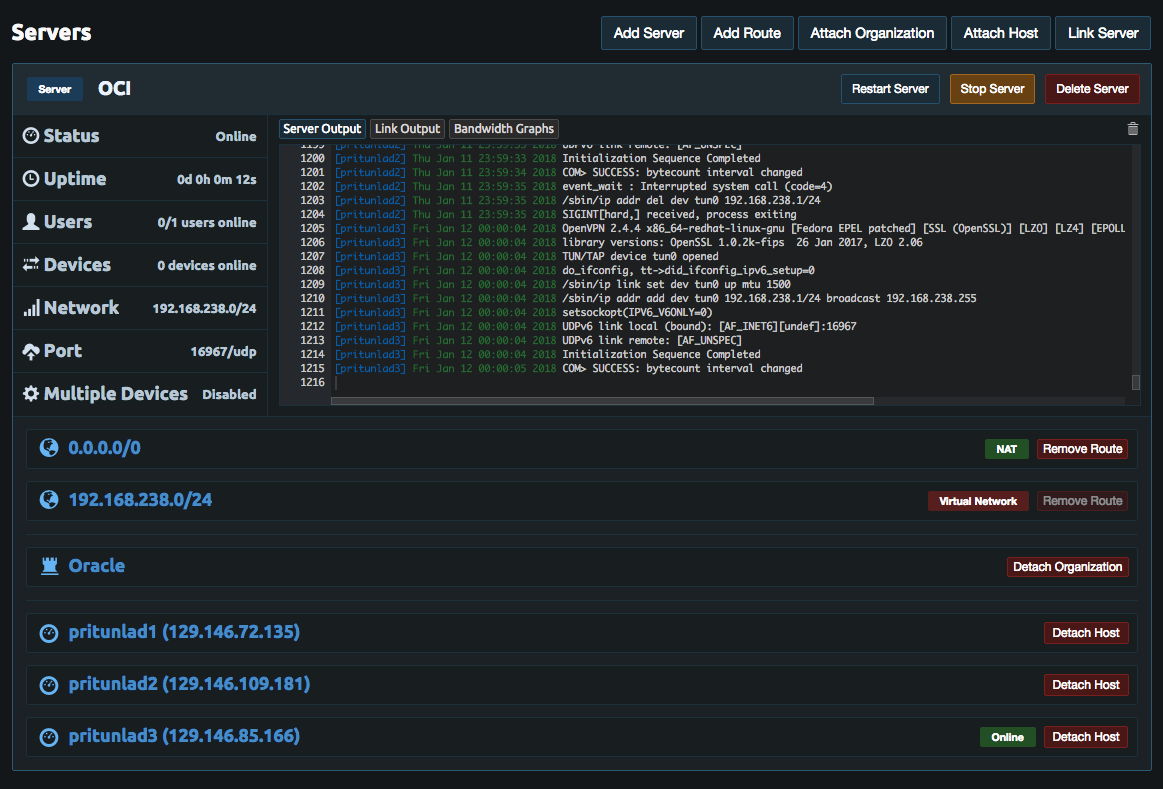
11e- Start the Pritunl Server
12- Now it’s time to test a client connection. Download the appropriate Pritunl Client based on your operating system, start it, and import the user profile that was created on step #11a.
Conclusion
Oracle Cloud Infrastructure is hosted in regions and Availability Domains. A region is a localized geographic area, and an Availability Domain is one or more data centers located within a region. A region is composed of several Availability Domains. Most bare metal resources are either region-specific, such as a virtual cloud network, or Availability Domain-specific, such as a compute instance.
Availability Domains are isolated from each other, fault tolerant, and very unlikely to fail simultaneously. Because Availability Domains do not share infrastructure such as power or cooling, or the internal Availability Domain network, a failure at one Availability Domain is unlikely to impact the availability of the others as stated in the public documentation.
Since Oracle Cloud Infrastructure provides a fault tolerant environment by default, your VPN configuration should provide a safe and reliable user data communication channel and be fault tolerant as well. The process outlined in this blog explained how to maintain the VPN encrypted channel communication running for both high-availability and disaster recovery in case a failure occurs.
Demonstration
Watch this Automatic VPN failover and Client Reconnection on Oracle Cloud Infrastructure video (4 minutes) to see how the failover happens automatically in the event of downtime, along with VPN client reconnection.
Additional Information
