Many Oracle Cloud Infrastructure customers have compute instances in virtual cloud networks (VCNs) that, for privacy, security, or operational concerns, are connected to private subnets. To grant these resources access to the public internet for software updates, CRL checks, and so on, a customer’s only option has been to create a NAT instance in a public subnet and route traffic through that instance by using its private IP address as a route target from within the private subnet. Although many have successfully used this approach, it does not scale easily and provides a myriad of administrative and operational challenges.
We are excited to announce the availability of NAT gateway, which addresses these challenges and provides Oracle Cloud Infrastructure customers with a simple and intuitive tool to address their networking security needs. NAT gateways provide the following features:
- Highly Scalable and Fully Managed: Instances on private subnets can initiate large numbers of connections to the public internet. Connections initiated from the internet are blocked.
- Secure: Traffic through NAT gateways can be disabled with the click of a button.
- Dedicated IP Addresses: Each NAT gateway is assigned a dedicated IP address that can be reliably added to security whitelists.
This rest of this post describes how to access the public internet from a private instance through a NAT gateway.
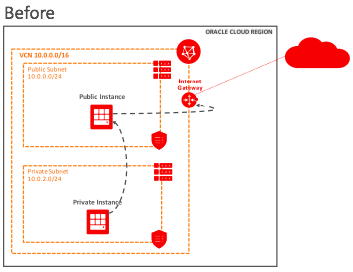
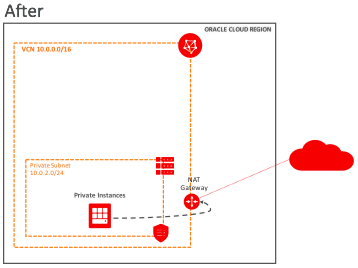
Before NAT gateway, a private instance accessed the public internet through a (public) NAT instance. The VCN had one public subnet and one private subnet with their associated route tables, security lists, and DHCP options.
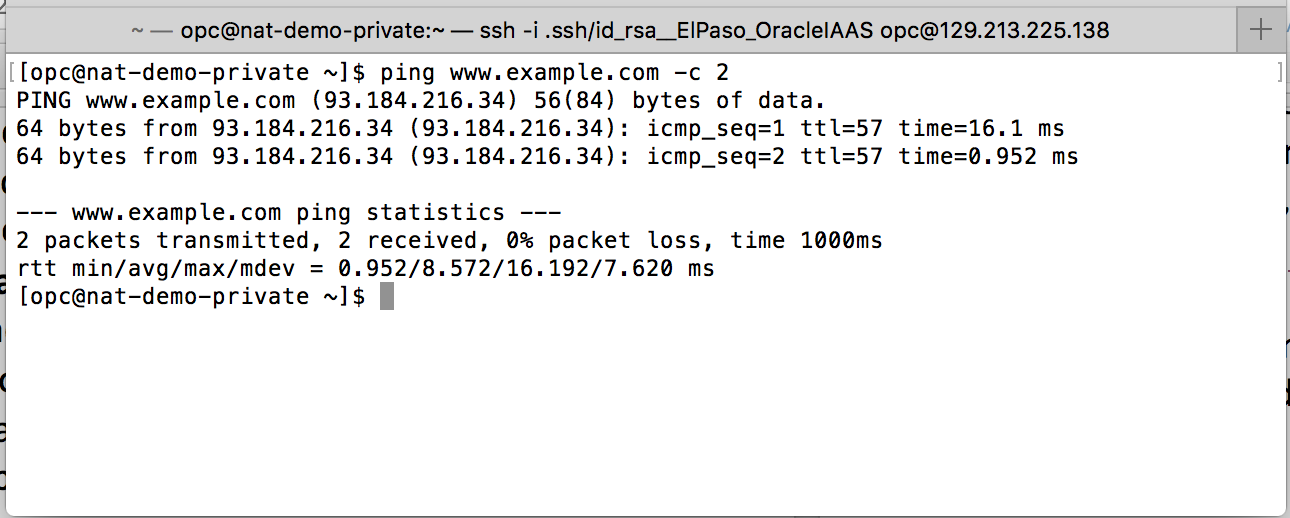
Through a bastion host (not shown), you used SSH to connect to the private instance and access resources on the public internet, as shown in the following example:
Now, you can create a NAT gateway in the VCN:
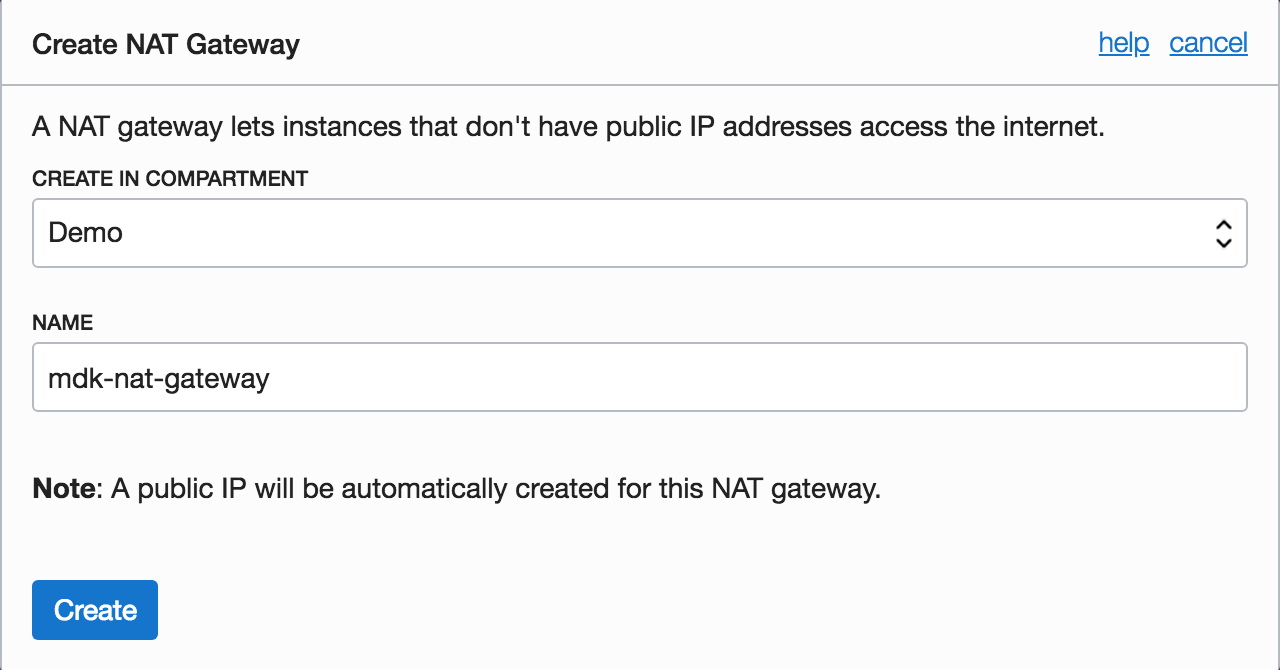
You can see the newly created gateway in the list of NAT gateways for the VCN:
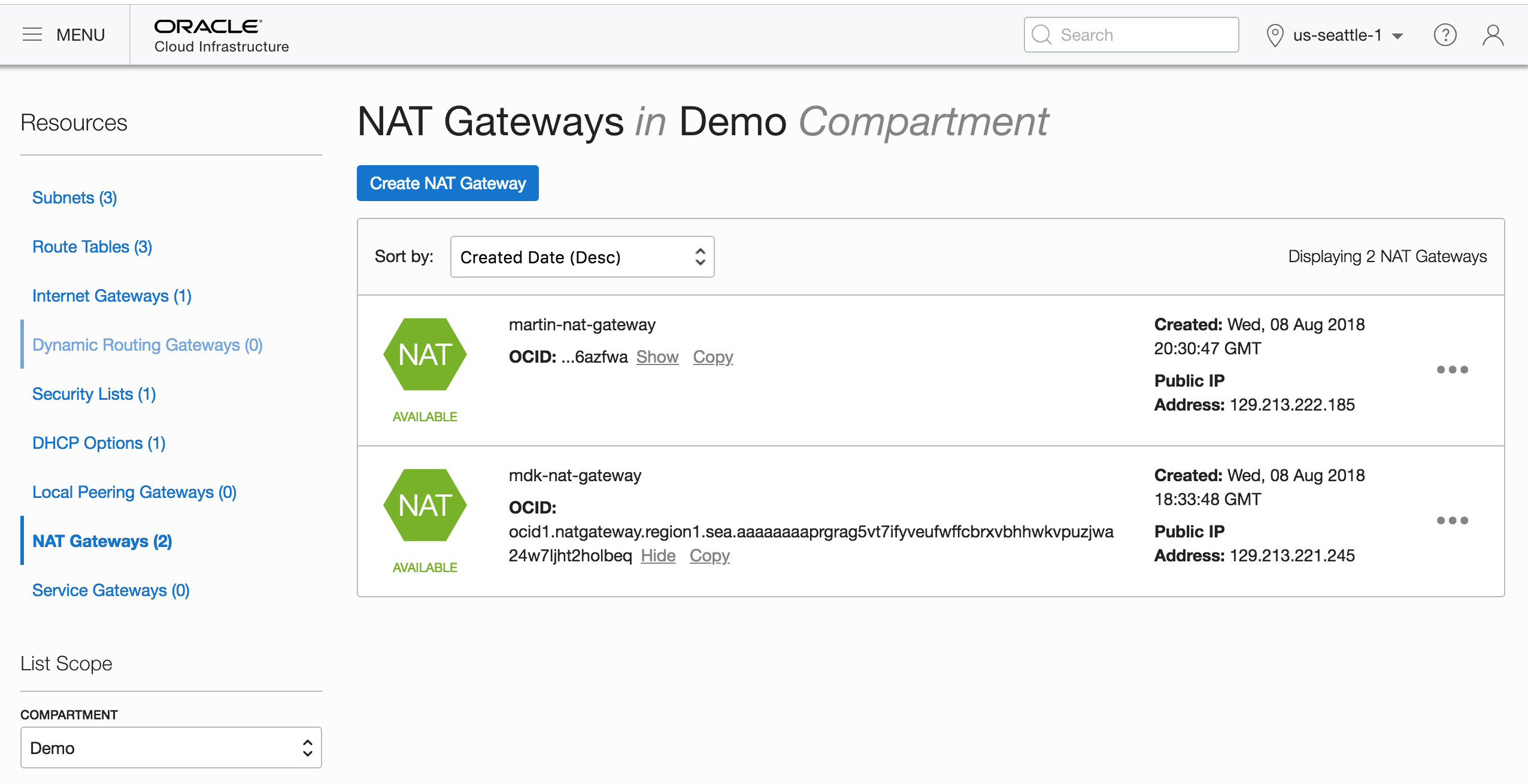
Finally, you replace the route rule that pointed to the NAT instance with one that points to the NAT gateway:
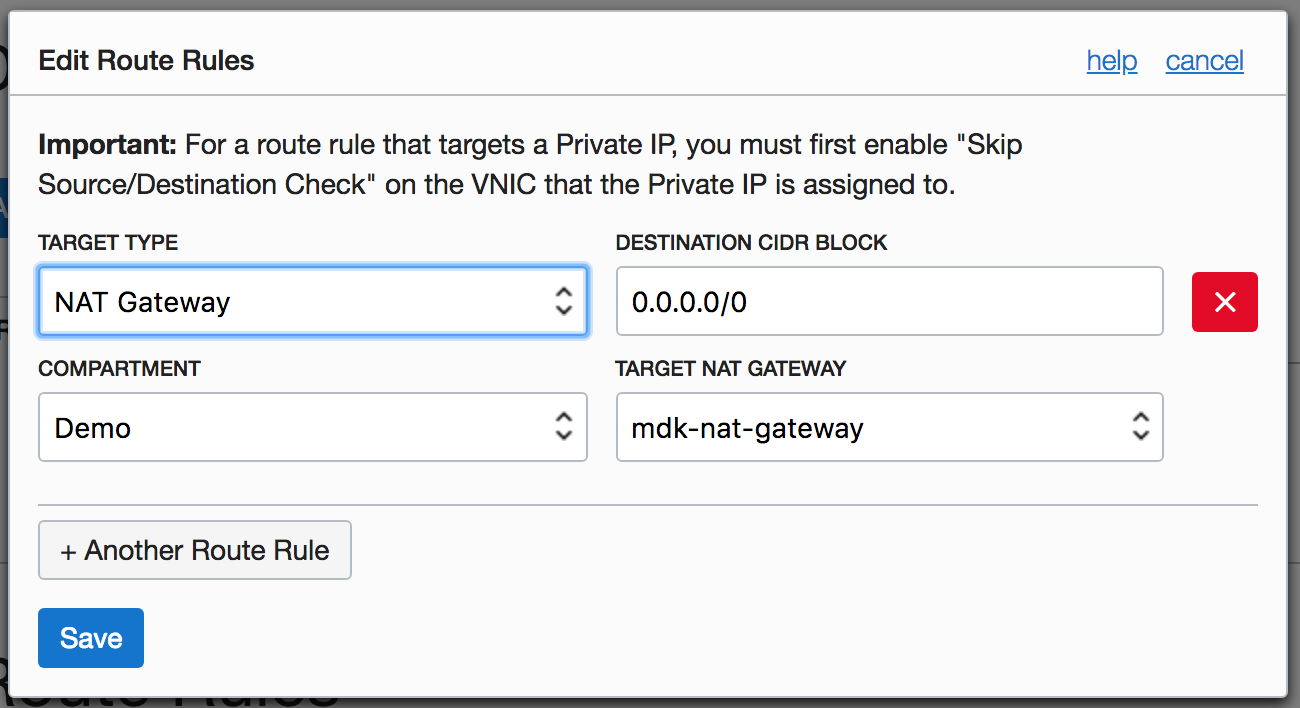
In just a few steps, you can give all the instances in the private subnet access to resources on the internet. As with the other Oracle Cloud Infrastructure gateways (Service, Internet, and so on), the NAT gateway is highly available and scales elastically to meet your bandwidth requirements. You can now delete the public NAT instance, which is no longer required.
We recommend NAT gateway as the preferred method for granting internet access to instances on private subnets. You can read more about NAT gateways in the Networking documentation. You can also watch our video demo for additional details.