Joint controller scenarios typically arise where large company shares their data with their partners for add-on services. If a breach occurs, all parties are liable—a huge concern for small and mid-size organizations, because the potential for financial impact is all the more consequential.
This post follows up on my previous post and digs deeper into the architecture and role of 0Chain, using a ledger and a single source of data solution to tackle joint controller scenarios. It covers the challenges posted by Europe’s General Data Protection Regulation (GDPR) and the Schrems II legal decision, which complicates EU-US data transfers.
Schrems II and what it means for privacy
Schrems II is a privacy ruling that has implications for companies that transfer any data from the EU to a US data center. That data can become subject to a government intervention and no longer be protected by prior privacy laws.
In such cases, 0Chain’s Privacy and Data Protection Platform (0Stor Private)— deployable from Oracle Cloud Marketplace—reduces risk by providing a clear demarcation between controllers with records of data activities, breach protection, and allows addressing Schrems II privacy issues. These solutions are complementary to Oracle Autonomous Database security, which provides critical features, such as automated patches and decoupled database management. For automated privacy and access settings for specific files at a certain cost, 0Stor can integrate with Oracle Blockchain Platform smart contracts to enable automated access tracking for users, lawyers, and auditors.
As noted by Mark Rakhmilevich, senior director of Oracle Blockchain Product Management, “0Stor Data Protection Platform with Oracle Blockchain Platform solve the challenge of private data storage with access auditing that is a cornerstone of many privacy initiatives, such as GDPR in Europe and CCPA in California. Transparency and immutability of access records is an important confidence-builder for users and can be a critical factor in any audits or lawsuits. 0Stor demarcated storage is a powerful solution for data privacy protection, and it can now be extended to provide blockchain anchored access records using Oracle blockchain.”
Current enterprise architecture
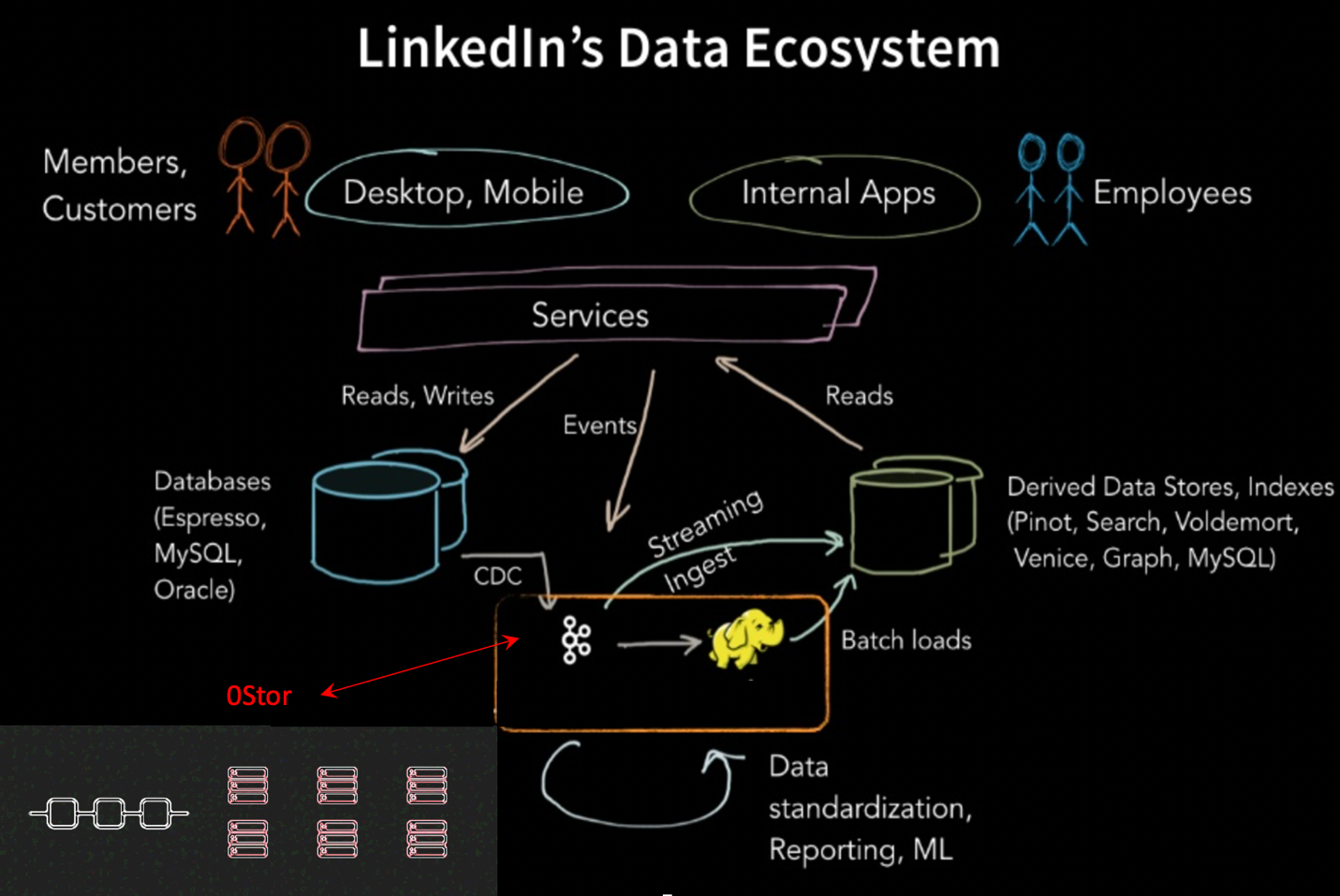
Most companies have an online-offline data model, as depicted in the architecture overview by Shirshanka Das of LinkedIn. In this architecture, data is sent from the online system to the offline through a streaming service, such as a Kafka data pipeline. The 0Chain platform is superimposed on the image in red at the bottom left to show how it would integrate with a typical enterprise system and can be viewed as another offline system.
The 0Chain solution
0Stor Private provides the following features:
- A transparent immutable ledger to track data movement between controllers and provide clear delineation of responsibility and liability if a breach occurs
- A breach protection platform for storing data A single source of truth instead of multiple copies in disparate systems which can be corrupted
Preventing internal breach
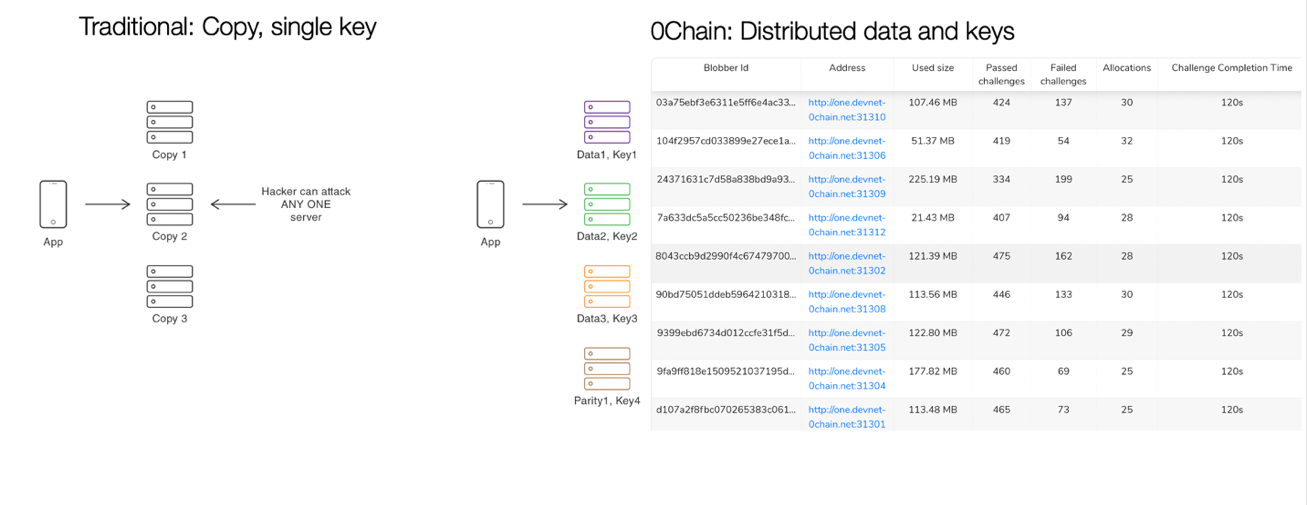
The following diagram shows how data at rest and in transit is secured by splitting the data up into pieces as it’s sent and stored in multiple servers with separate keys. Unlike the traditional replication scheme, the hacker can’t attack one server alone but needs multiple keys to access the content.
The data is shared through authtoken to an application or entity. That entity can download the data and decrypt it with their private key. So, the entity needs to protect their key to prevent hacking. While it’s outside the scope of this post, 0Chain offers a split key technology that can protect the key from being misused.
Burden of liability and walled privacy
The burden of liability for a joint controller is determined from an immutable record of data activities. If all controllers have their own 0Stor platform that records data acquired from other controllers, then they’re protected against any joint liability. They can provide bullet-proof arguments to show that the security of data and privacy isn’t compromised during a breach event. This architecture can be described as a “walled privacy,” where each controller has their individual repository and audit trail when interacting with other controllers and can control their liability risk.
0Chain benefits
The 0Stor Private platform provides the following benefits:
- Reduces joint controller-based risks: Each controller deploys a 0Stor Private platform, records data activity events, provides internal breach security, and can establish and prove clear demarcation of data ingress and deletion during a breach event.
- Abides by SchremsII ruling with minimal changes: The controller needs to allow an option to own and control data, a mechanism that’s automated using the 0Stor Private platform.
- Lower legal cost: The 0Chain ledger automatically provides a transparent data audit capability for anyone, including users and lawyers. So, there are no discovery costs for either party.
- Internal breach protection: Encrypted data is split into shards in different servers with separate keys. A hacker inside the company would need to get all the keys to breach the content, which is a near impossibility.
Enterprise integration
The following diagram shows the architecture of how 0Chain interact with the enterprise system. You can view the 0Stor Private platform as an external offline system connected to a Kafka service of the enterprise. It’s first in line to consume the data and publish an authentication token for other offline services to retrieve the data directly from 0Stor. The data stays inside 0Stor, assured of its internal breach security and privacy, and can be directly accessed from other offline systems, third-party partners, and so on.
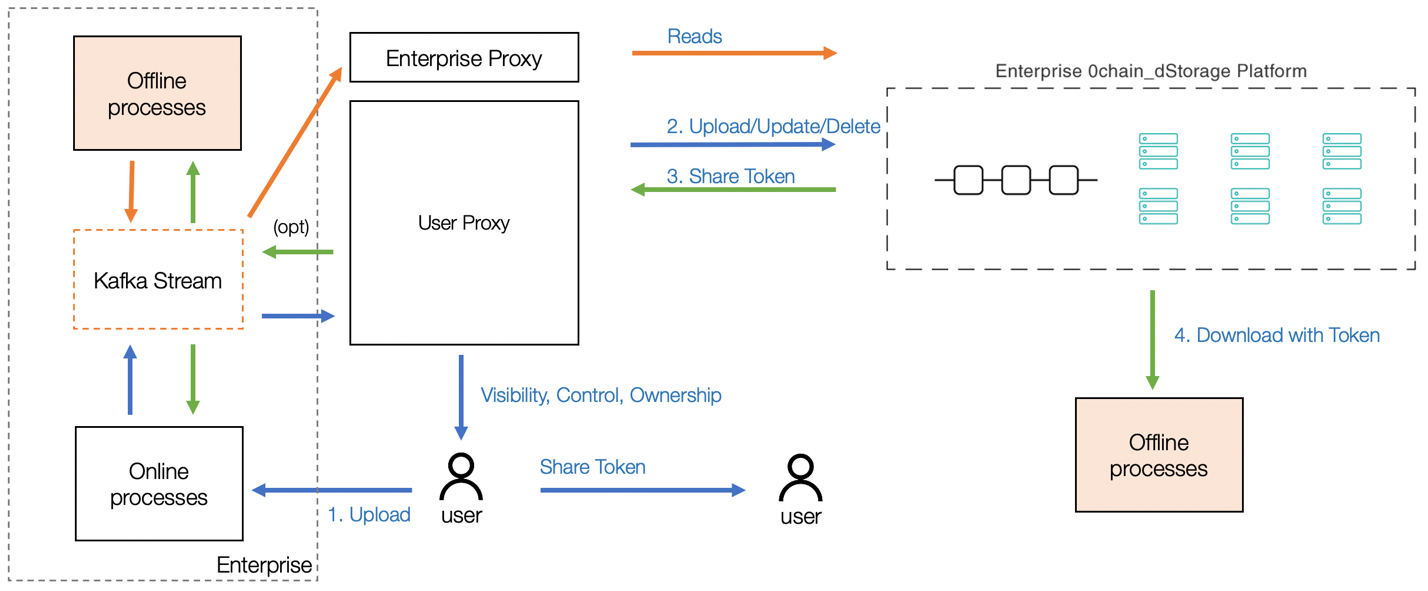
- The diagram shows the following steps for deployment:
- The customer uploads data through an existing frontend.
- When it enters the Kafka stream, userProxy consumes it and uploads to 0Stor.
- userProxy then publishes tokens for different offline services that consume user data.
The offline services can then directly download the data from 0Stor using the token. As a result, the reads are stamped on the 0Chain ledger.
The process accomplishes the following things:
- Liability for the controller is reduced as all activities are transparent and immutably recorded on the ledger.
- The customer has full visibility on activities using their data.
Conclusion
To combat the recent Schrems II ruling and joint controller GDPR issues, enterprises can deploy a 0Stor Private easily on Oracle Cloud Infrastructure, integrate through Kafka data pipelines, and have total control over the security and privacy of data and substantially reducing their liability risk.
Ready to try 0Stor Private for yourself? Visit the listing on Oracle Cloud Marketplace today!