Original Publish date : 7/15/2015
AD Machine (Windows Server 2012 R2) used in this configuration is : slads.slab.bea.com
WLS 10.3.6 is installed on AIX 6.1 : celbealnx4.us.oracle.com
kerberos_aix is the user created in AD which will represent the weblogic server machine.
*****************************
Step 1 :
– Create a new user say, ” kerberos_aix ” on AD which will represent your Weblogic server instance.
Note :
– The account type should be “User”, not a “Computer” in the AD.
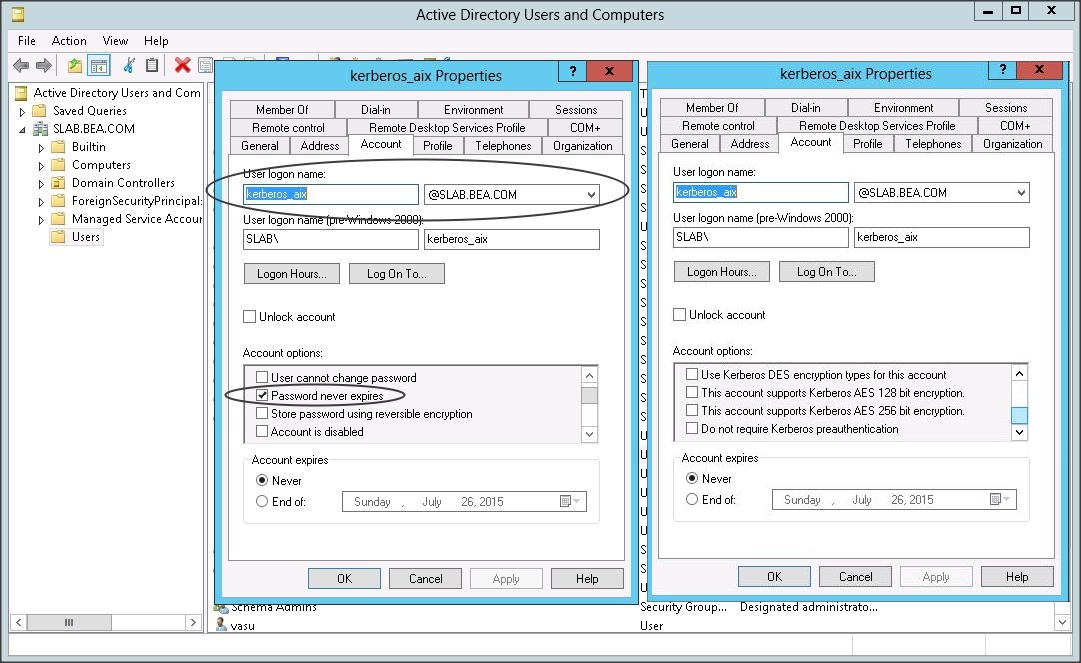
– Check password never expires option for the user.
– DES encryption type is disabled by default on Windows 2008 AD and above and hence do not check this option for the user.
– If your AD is on Windows 2003, enable DES encyption type for your user –> after enabling this option make sure you reset the password for this user.
– If you want to use AES encryption type make sure you check ” This account supports AES 128 bit encryption “/ “This account supports AES 256 bit encryption “ in the username –> properties –> Account Options field.
– If you want to use AES256-SHA1 cipher strength then,
You need to download and install this bundle which provides “unlimited strength” policy files which contain no restrictions on cryptographic strengths.
* For IBM JDK 6 and above: Download Java Cryptography Extension (JCE) Unlimited Strength Jurisdiction Policy Files from :
https://www-01.ibm.com/marketing/iwm/iwm/web/preLogin.do?source=jcesdk
< Additional Info >
http://goo.gl/XZRasJ
Step 2 :
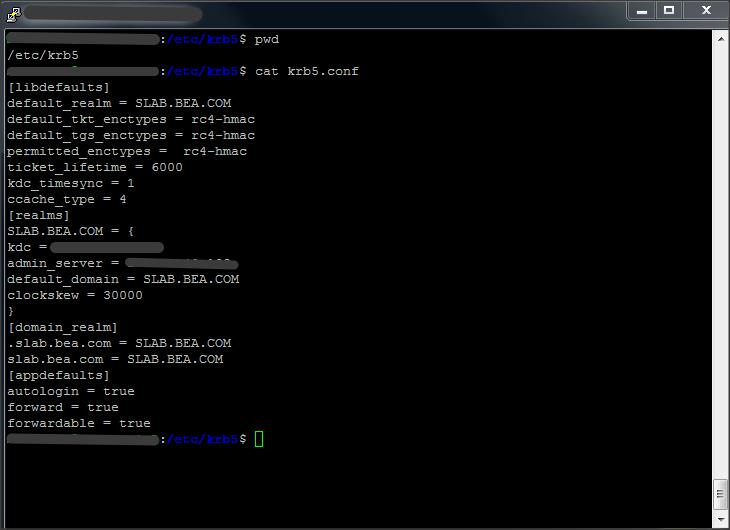
Create a krb5.conf file.
Syntax :
*****
[libdefaults]
default_realm = <Identifies the default realm. Set its value to your Kerberos realm – all caps>
default_tkt_enctypes = aes256-cts-hmac-sha1-96 rc4-hmac des-cbc-crc des-cbc-md5
default_tgs_enctypes = aes256-cts-hmac-sha1-96 rc4-hmac des-cbc-crc des-cbc-md5
permitted_enctypes = aes256-cts-hmac-sha1-96 rc4-hmac des-cbc-crc des-cbc-md5
ticket_lifetime = 600
kdc_timesync = 1
ccache_type = 4
[realms]
<Your Kerberos realm – remember all caps> = {
kdc = <IP address of the KDC/AD server>
admin_server = <FQDN – host name of the KDC/AD server OR IP address of KDC/AD server>
default_domain = <Windows domain name in caps>
}
[domain_realm]
.<DNS domain name suffix, starting with .> = <Your Kerberos realm – remember all caps>
<DNS domain name suffix.> = <Your Kerberos realm – remember all caps>
[appdefaults]
autologin = true
forward = true
forwardable = true
encrypt = true
*****
Note :
* This file has to be created on the machine where Weblogic Server is installed. In this case it is present in AIX 6.1 machine.
* In AIX machine, the default location is /etc/krb5/krb5.conf.
* It is always good to specify only the encryption type that is needed in default_tkt_enctypes and default_tgs_enctypes. For example rc4-hmac in this case. (have a look at the above screenshot).
DOWNLOAD A SAMPLE OF KRB5.CONF
Step 3 :
Lets check if your AIX box is able to communicate with the KDC using the information provided in the krb5.conf :
Command : kinit kerberos_aix OR kinit kerberos_aix @<REALM>
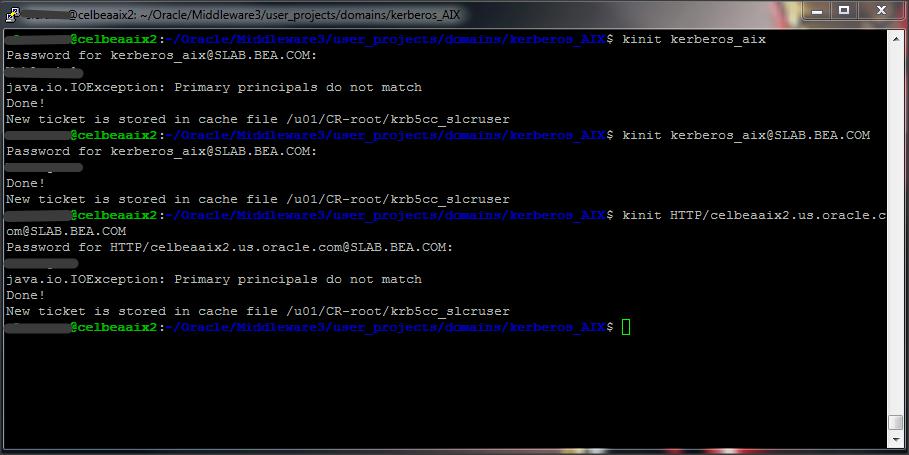
Step 4 :
( Run the following commands on AD machine ).
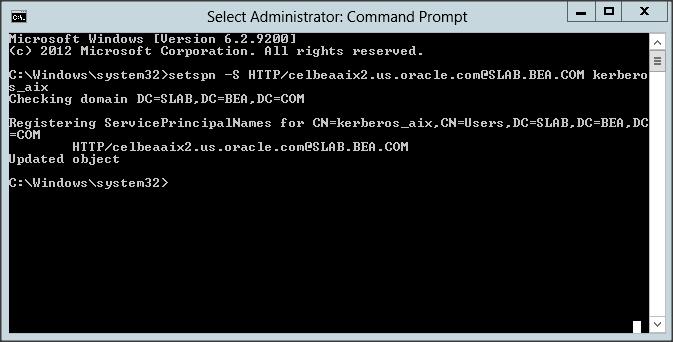
Lets make sure that there are no duplicate SPNs in your AD box and then add an SPN to ” kerberos_aix” user :
Syntax : setspn -S HTTP/<wls-server-name>@<REALM-NAME> <account_name>
Command : setspn -S HTTP/celbeaaix2.us.oracle.com@SLAB.BEA.COM kerberos_aix
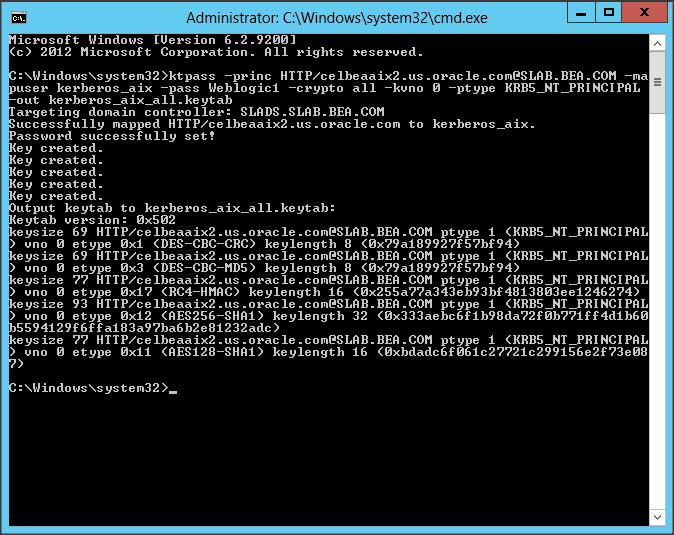
Now lets create a keytab file :
Syntax : ktpass –princ HTTP/<wls-server-name>@<REALM-NAME> -mapuser <account-name> –pass password -crypto all -kvno 0 -ptype KRB5_NT_PRINCIPAL –out <keytab-file-name>
Command : ktpass -princ HTTP/SLKRBTRN6-03@SLKRBTRN6.BEA.COM -mapuser wlsclient -pass Weblogic1 -crypto Rc4-HMAC-NT -kvno 0 -ptype KRB5_NT_PRINCIPAL -out kerberos_aix_rc4.keytab
Note :
* Running ktpass will modify the account details, changing the user login name to match the service principal name – note that this is a consequence of running the above command, not something you need to do manually
* Click on the user ” kerberos_aix ” properties to see the change.
* Now copy the keytab file generated (kerberos_aix_rc4.keytab) to machine where Weblogic Server is installed.
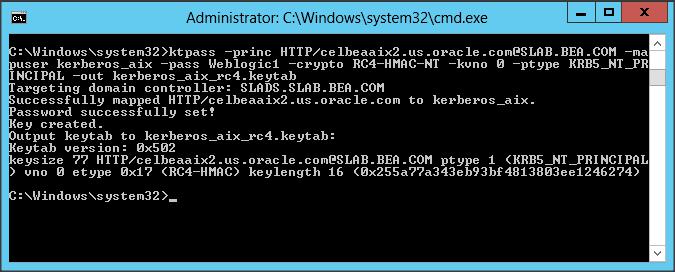
* If you are using Windows 2003 AD then use the following command :
ktpass –princ HTTP/<wls-server-name>@<REALM-NAME> -mapuser <account-name> –pass password -crypto DES-CBC-CRC -ptype KRB5_NT_PRINCIPAL –out <keytab-file-name>
* In the above command you can use “-crpto all” but there are few IBM JDK bugs which cause the JASS config to always look into the first encryption type available in the keytab and will fail saying it was not able to find RC4-HMAC. This is fixed in the latest versions of JDK, however it is safe to create a keytab containing only the required encryption type ” -crypto RC4-HMAC-NT “.
Step 5 :
After copying the keytab file to the machine where Weblogic Server is installed, run the klist command to see the contents of the keytab file.
Syntax : klist -k <keytab>
Command : klist -e -k kerberos_aix_rc4.keytab
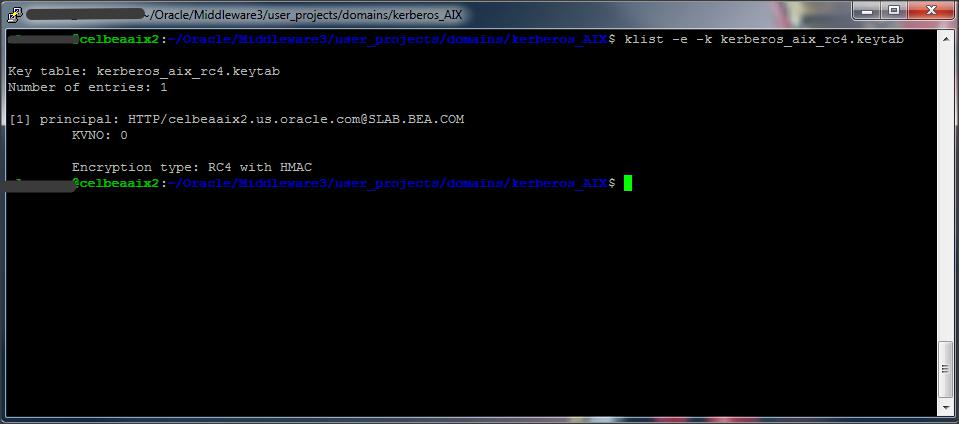
If your principal was created properly, you should be able to request a TGT (ticket Granting Ticket) from Kerberos using that principal.
If the keytab file was generated properly, then you should be able to use this file instead of the password of your account. kinit tests both simultaneously.
Syntax : kinit –k –t <keytab-file> <account-name>
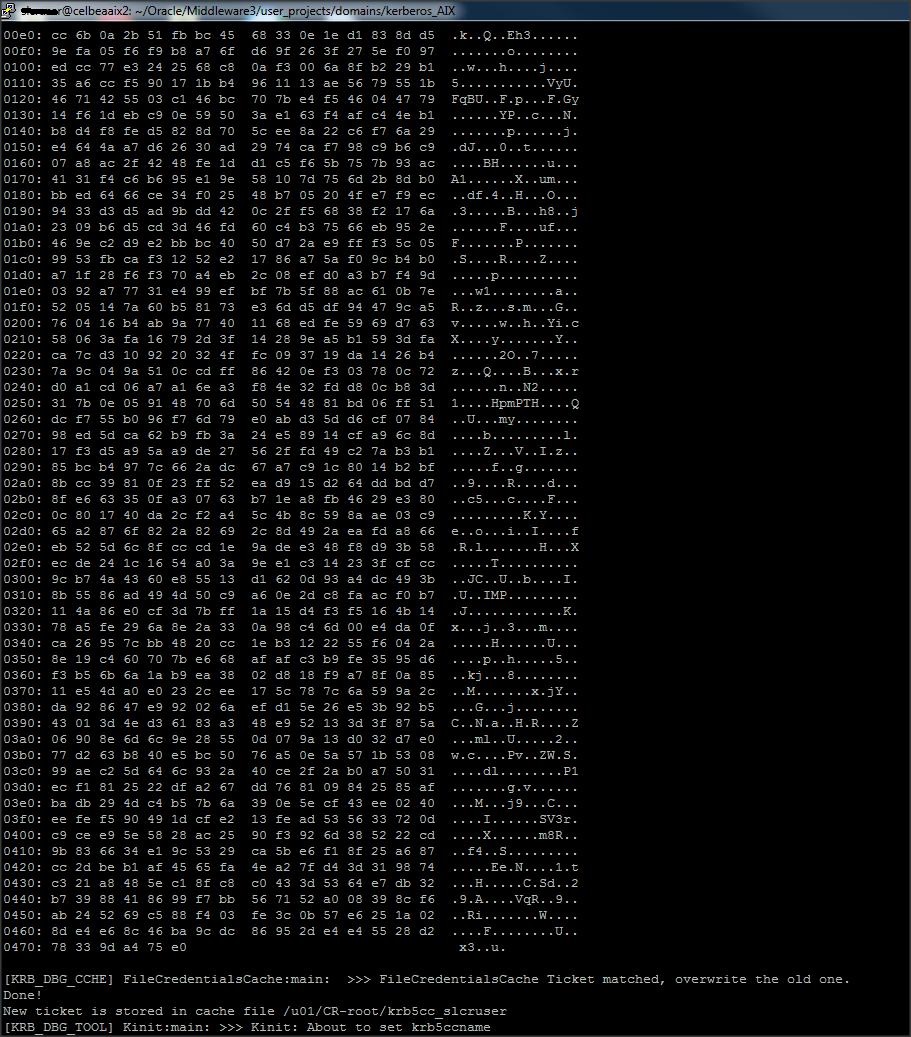
Command : kinit -k -t kerberos_aix_rc4.keytab HTTP/celbeaaix2.us.oracle.com@SLAB.BEA.COM
Output :
Done!
New ticket is stored in cache file /u01/CR-root/krb5cc_slcruser
Now lets enable few debugs to get a detailed output :
Command :
java -Dcom.ibm.security.jgss.debug=all -Dcom.ibm.security.krb5.Krb5Debug=all com.ibm.security.krb5.internal.tools.Kinit -k -t kerberos_aix_rc4.keytab HTTP/celbeaaix2.us.oracle.com@SLAB.BEA.COM
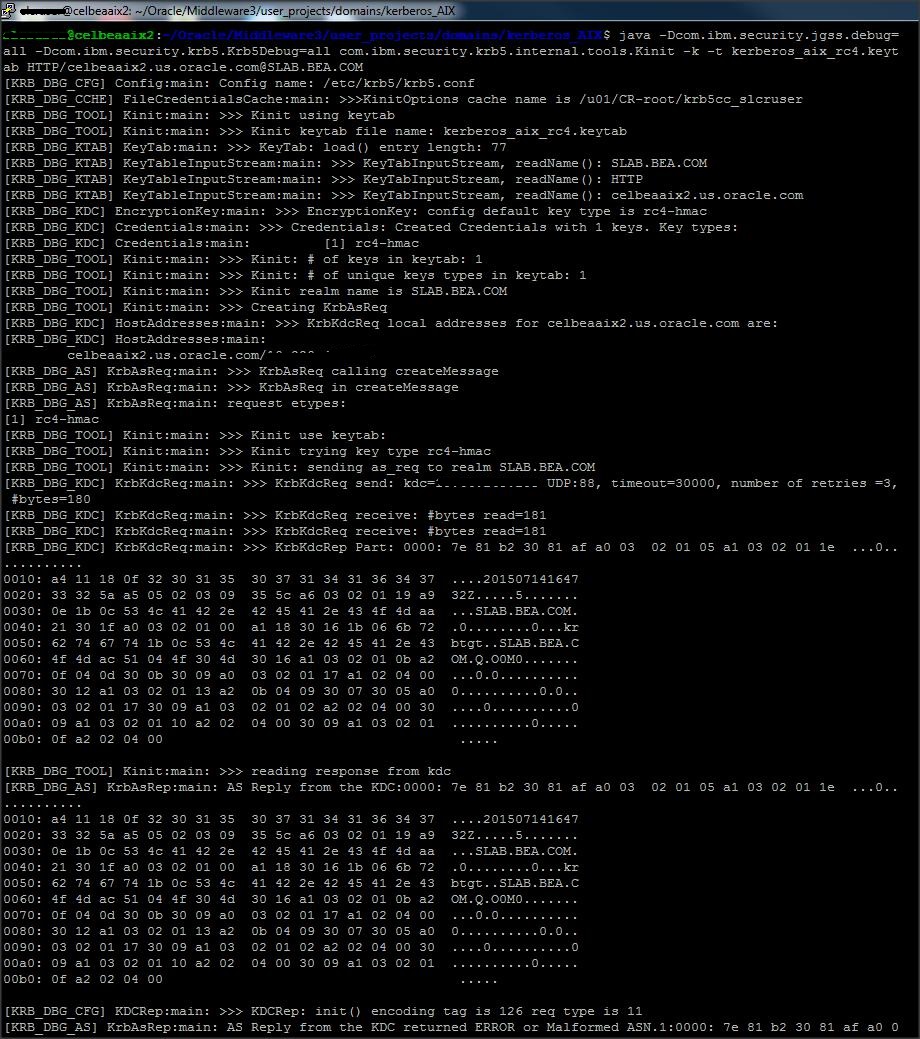
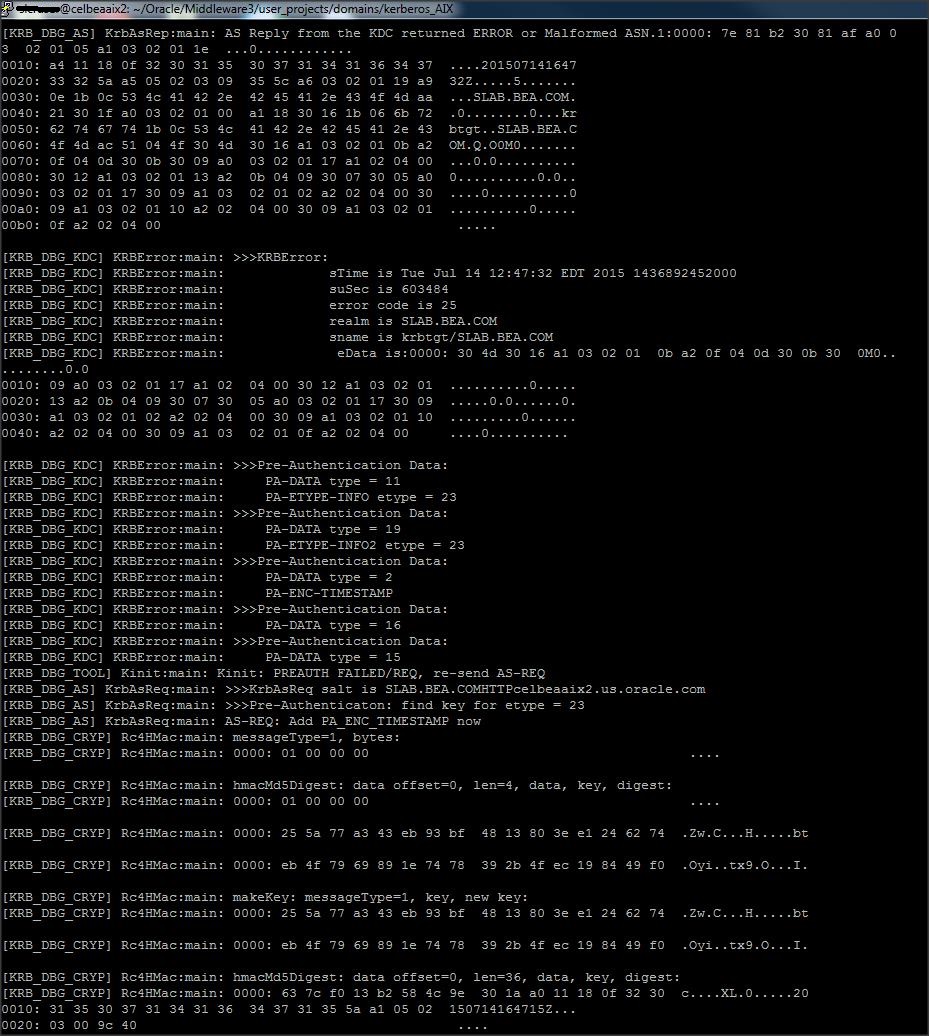
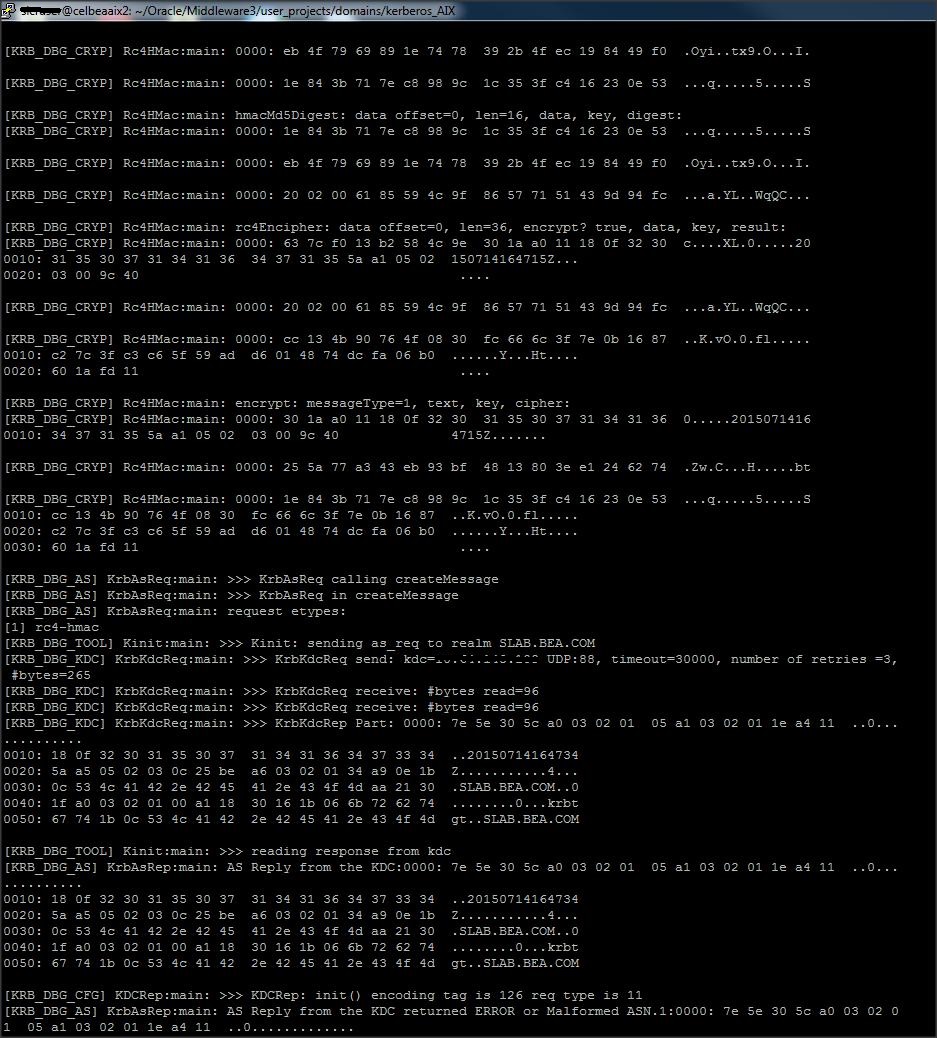
Note :
* When you lock and unlock your computer, you are causing Windows to request new Kerberos tickets. Another way to force Windows to request new Kerberos tickets is to run ” klist purge ” from the command prompt. This explicitly asks Windows to dump your currently Kerberos tickets and thus, request new ones.
Step 6 :
Now, lets create a JAAS config file, that will be used by Weblogic server :
Create a file called ” krb5Login.conf ” and place it in the Weblogic Server domain directory :
Syntax :
Have a look at the following doc for list of supported and unsupported parameters in JAAS config file :
http://www-01.ibm.com/support/knowledgecenter/SSYKE2_7.0.0/com.ibm.java.security.component.70.doc/security-component/jgssDocs/jaas_login_user.html
Example :
com.ibm.security.jgss.initiate {
com.ibm.security.auth.module.Krb5LoginModule required
credsType=initiator
debug=true;
};
com.ibm.security.jgss.krb5.accept {
com.ibm.security.auth.module.Krb5LoginModule required
principal=”HTTP/celbeaaix2.us.oracle.com@SLAB.BEA.COM”
useKeytab=”file:/refresh/CR-root/Oracle/Middleware3/user_projects/domains/kerberos_AIX/kerberos_aix_rc4.keytab”
credsType=acceptor
debug=true;
};
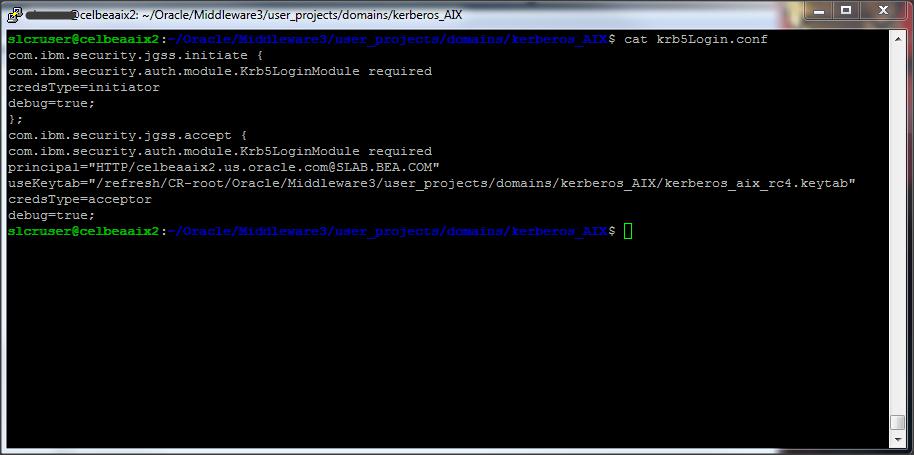
DOWNLOAD A SAMPLE OF KRB5LOGIN.CONF
Step 7 :
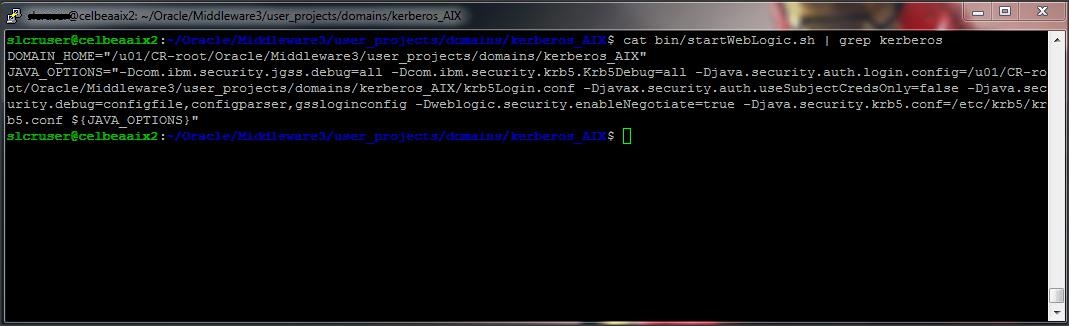
Now lets add few -D parameters to Weblogic Server startup script :
-Djava.security.auth.login.config=krb5Login.conf
-Djavax.security.auth.useSubjectCredsOnly=false
-Djava.security.krb5.conf=/etc/krb5/krb5.conf
-Dweblogic.security.enableNegotiate=true
DEBUG Flags :
-Dcom.ibm.security.jgss.debug=all
-Djava.security.debug=configfile,configparser,gssloginconfig
-Dcom.ibm.security.krb5.Krb5Debug=all
OPTIONAL Flags :
-Djava.security.krb5.realm=<realm>
-Djava.security.krb5.kdc=<kdc>
Example :
JAVA_OPTIONS=”-Dcom.ibm.security.jgss.debug=all -Djava.security.auth.login.config=/u01/CR-root/Oracle/Middleware3/user_projects/domains/kerberos_AIX/krb5Login.conf -Djavax.security.auth.useSubjectCredsOnly=false -Djava.security.debug=configfile,configparser,gssloginconfig -Dcom.ibm.security.krb5.Krb5Debug=all -Dweblogic.security.enableNegotiate=true -Djava.security.krb5.conf=/etc/krb5/krb5.conf ${JAVA_OPTIONS}”
export JAVA_OPTIONS
Step 8 :
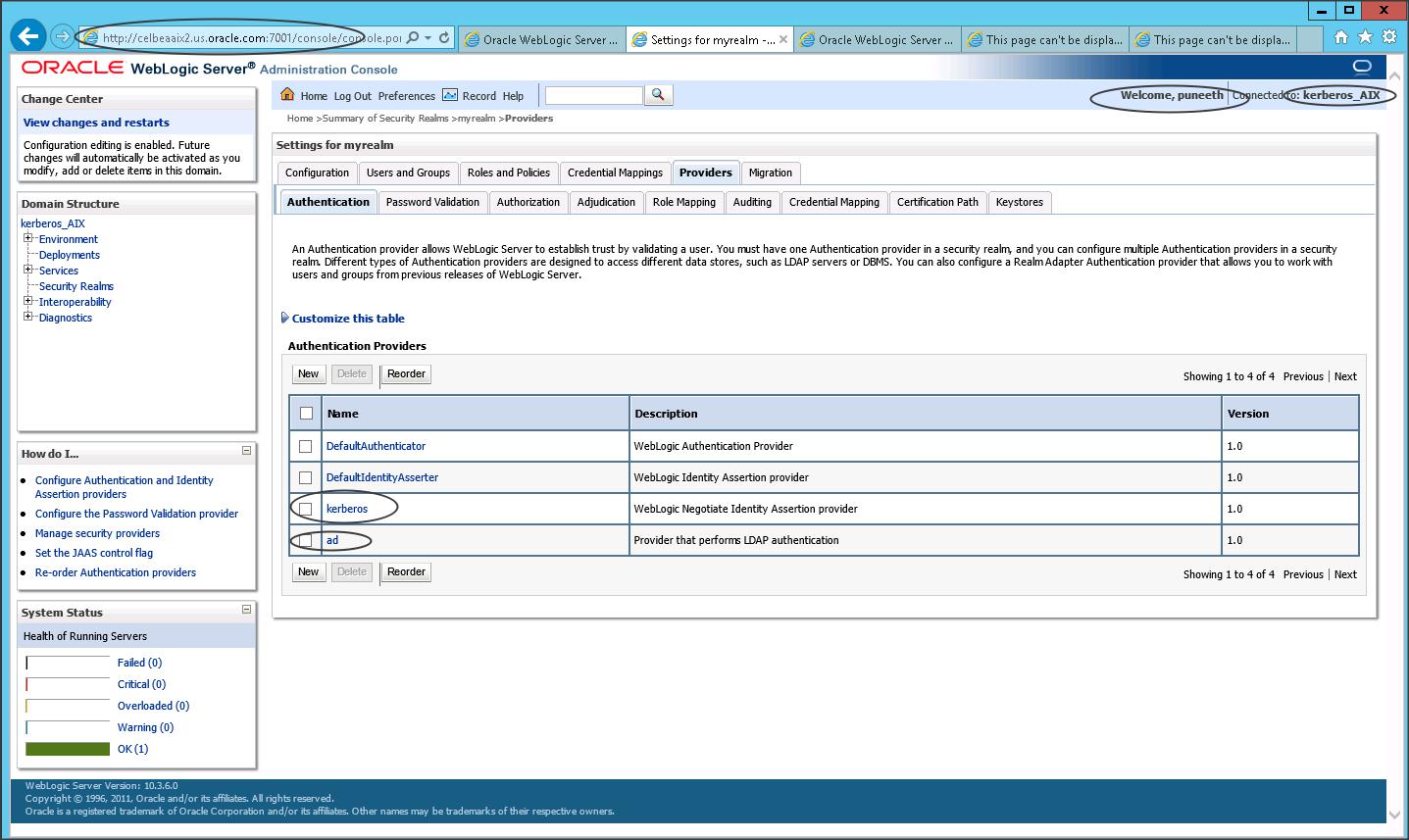
Login to weblogic console and configure Active Directory provider.
Change the control flags of all the providers to ” Optional “.
If you have set control flag as sufficient then reorder the providers and make sure Active Directory providers is the first provider in the list.
Step 9 :
Now, create a ” NegotiateIdentityAsserter ”
Step 10 :
Setup your browser for Kerberos Authentication.
* No special configuration needed for Chrome Browser.
* For Mozilla Firefox browser :
1. Start Firefox.
2. Enter about:config in the Location Bar.
3. Enter the filter string network.negotiate.
4. Double click on network.negotitate-auth.delegation-uris and enter ” http://,https:// “
5. Double click on network.negotitate-auth.trusted-uris and enter ” http://,https:// ”
* For Internet Explorer :
Configure Local Intranet Domains
1. In Internet Explorer, select Tools > Internet Options.
2. Select the Security tab.
3. Select Local intranet and click Sites.
4. In the Local intranet popup, ensure that the Include all sites that bypass the proxy server and Include all local (intranet) sites not listed in other zones options are checked.
5. Click Advanced.
6. In the Local intranet (Advanced) dialog box, add all relative domain names that will be used for Oracle WebLogic Server instances participating in the SSO configuration (for example, myhost.example.com) and click OK.
Configure Intranet Authentication
1. Select Tools > Internet Options.
2. Select the Security tab.
3. Select Local intranet and click Custom Level… .
4. In the Security Settings dialog box, scroll to the User Authentication section.
5. Select Automatic logon only in Intranet zone. This option prevents users from having to re-enter logon credentials, which is a key piece to this solution.
6. Click OK.
Now, when you access your Weblogic Admin Console, you should be able to login to it without entering a username / password.