![]()
This blog describes how to set up SAML 2.0 Single Sign-on (SSO) for Oracle Analytics Server (OAS) without using a Docker container.
The way you configure SAML 2.0 SSO for OAS is different to Oracle Business Intelligence Enterprise Edition (OBIEE). With OAS, you mustn’t modify or customize binary files such as .ear files and domain home configuration files. This solution uses Apache HTTP server operating on Oracle Enterprise Linux 7/8 or Red Hat Enterprise Linux 7/8 with the mod_auth_mellon authentication module.
Prerequisites
- Oracle Analytics Server (version 5.9.0 or higher).
- In Oracle WebLogic Server administration console, the same user store available at the SAML IdP is configured as an authentication provider.
- If the Oracle WebLogic Server doesn’t have an external authenticator, configure OAS to use the same users and groups in the WebLogic embedded LDAP that the SAML IdP will send upon successful authentication.
- Oracle WebLogic Server configured with an identity asserter, such as Oracle Access Manager Identity Asserter (OAMIdentityAsserter) for OAS.
Configuration Overview
- Configure Apache HTTP server as an OAS proxy server.
- Install mod_auth_mellon on the Apache HTTP server and configure the plugin on the web server.
- Configure SAML SP with SAML IdP.
- Configure the Protected, Public, Excluded Resources list in the Apache HTTP server with the AuthType as mellon.
- Configure an OAM Identity Asserter in OAS WebLogic Server.
- In Fusion Middleware Enterprise Manager, configure the SSO logout URL.
Authentication Flow
This sequence diagram shows the authentication flow and communication between the browser, Apache HTTP server, SAML Identity Provider, and the Oracle WebLogic Server on which Oracle Analytics Server is installed. The diagram doesn’t show the precise communication that occurs between the browser, the Apache HTTP server, the Oracle Analytics Server, and any SAML 2.0 compatible identity provider.
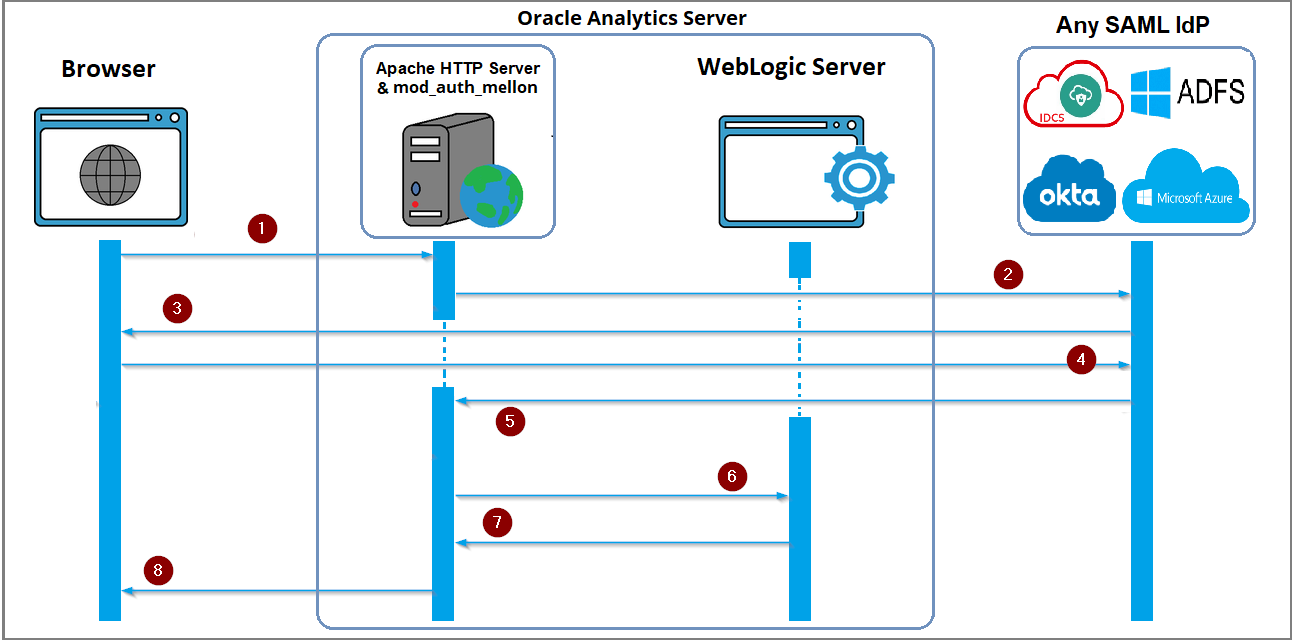
- The user navigates to the OAS URL in the browser using the Apache HTTP server (/dv or /analytics).
- If the resource is a protected resource, the Apache HTTP server’s authentication module (mellon) refers the user to the SAML identity provider for authentication.
- For authentication, the SAML identity provider displays the SSO login page in the browser or utilizes the authentication mechanism set for the SAML identity provider.
- The user submits login credentials to the SAML identity provider.
- After successful authentication, the SAML identity provider delivers the authenticated user in a SAML response to the service provider (an Apache HTTP server with mod_auth_mellon).
- The service provider delivers the user ID to Oracle WebLogic in an HTTP header called OAM_REMOTE_USER.
- Oracle WebLogic Server uses the Oracle Access Manager Identity Asserter (OAMIdentityAsserter) to retrieve the user ID from the HTTP header. If the user exists, OAS grants the user the application roles and grants access to the desired resource (/dv or /analytics) through the web server.
- The web server displays the requested resource in the user’s browser.
![]()
Considerations
Oracle recommends that you utilize the reference implementation for custom SAML 2.0 SSO, which is available as a Docker-based solution for OAS. This approach uses a web tier and a WebLogic asserter. See SAML 2.0 and Kerberos Single Sign-On Configuration for Oracle Analytics Server (Doc ID 2761678.1).
OAM_REMOTE_USER, iv-user, and SM_USER are the supported headers available at OAM Identity Asserter.
To prevent improper access, Oracle advises that you restrict direct access for all end users to the Oracle WebLogic managed server hosting OAS (bi_serverN) on port 9502.
End users must use the Apache HTTP server to reach the OAS URL.
Specific resources are intentionally left unprotected by the mod_auth_mellon module. These resources are accessible through the basic authentication mechanism (user ID and password) of OAS and are intended for usage by tools that can’t use SSO.
Approach
For this SSO solution, Apache HTTP Server (httpd) with the mod_auth_mellon authentication module is deployed in front of OAS.
The Apache HTTP Server performs SAML 2.0 SSO authentication and provides the successfully authenticated user’s user ID to the Oracle WebLogic Server, which hosts OAS.
Oracle WebLogic Server is configured with an Identity Asserter (such as OAMIdentityAsserter) to receive the user ID and assert the user just like a regular Oracle Access Manager (OAM) based SSO configuration. Consequently, this approach is a regular OAM (HTTP header-based SSO) solution as far as OAS is aware, meaning that all functionality certified for regular SSO also works with this approach.
The Apache HTTP Server with the required mod_auth_mellon authentication module must be installed on the same or a separate compute from the OAS server.
Protected, Public, and Excluded List of Resources for OAS
See, Updating the Protected, Public, and Excluded Resources for an Enterprise Deployment.
Configuration Instructions
My Oracle Support has instructions for configuring SAML 2.0 SSO for OAS using the Mellon authentication module and the Apache HTTP server. See the knowledge document ID 2902159.1, Configuring Oracle Analytics Server for SAML 2.0 Single Sign-On (SSO) Using Mellon Authentication Module of Apache HTTP Server (DocID 2902159.1).
Call to Action
In this blog post, you learned how to configure SAML 2.0 SSO for OAS using the Apache HTTP server and its authentication module, mod_auth_mellon. To handle SAML 2.0 SSO, the Apache HTTP Server employs the mod_auth_mellon module. Other SSO techniques for OAS are encouraged. SAML 2.0 and Kerberos Single Sign-On configuration for Oracle Analytics Server is the suggested approach for SSO.
![]()
