Introduction
The blog post Automate Oracle Analytics Cloud snapshot and data file migration using REST APIs discussed how to use OAuth tokens for REST APIs and Data File Migration Utility and automate the process using automation scripts. These scripts have plain text values of user names and passwords as input values for some variables. To avoid plain text values of sensitive data and use encrypted values in the scripts, use vaults and secrets in Oracle Cloud Infrastructure (OCI).
You use commands in the Oracle Cloud Infrastructure Command Line Interface (OCI CLI) in the scripts to read the encrypted values from OCI vaults and secrets. You need the prerequisites listed in the blog post Automate Oracle Analytics Cloud snapshot and data file migration using REST APIs for automation scripts.
Install OCI CLI
You can follow this blog post to install OCI CLI. Follow the cli install steps for all operating systems such as Linux, MacOS, and Windows.
Policies needed to access vaults and secrets
An administrator must have these policies:
- Allow group Admins to manage vaults in tenancy
- Allow group Admins to manage keys in tenancy
- Allow group Admins to manage secret-family in tenancy
A user must have the following policy to access all secrets in a compartment or a particular secret in a compartment:
Allow group users to read secret-family in compartment “oacauto”
or
Allow group users to read secret-family in compartment “oacauto” where target.secret.name is “AdminUserPwd”
Create vaults and secrets
To store sensitive data and call the values at runtime, you can create secrets and encrypt them with an Oracle-provided key or a customer key and store them in vaults. Using the OCI CLI, you can call the values of the secrets and use them in the automation scripts. You can create the secrets in plain text or base64 encoded values.
Create a vault, encryption key, and secrets:
- Log in to the OCI console.
- Navigate to Identity & Security and select Vault.
- Select the compartment.
- Click Create Vault.
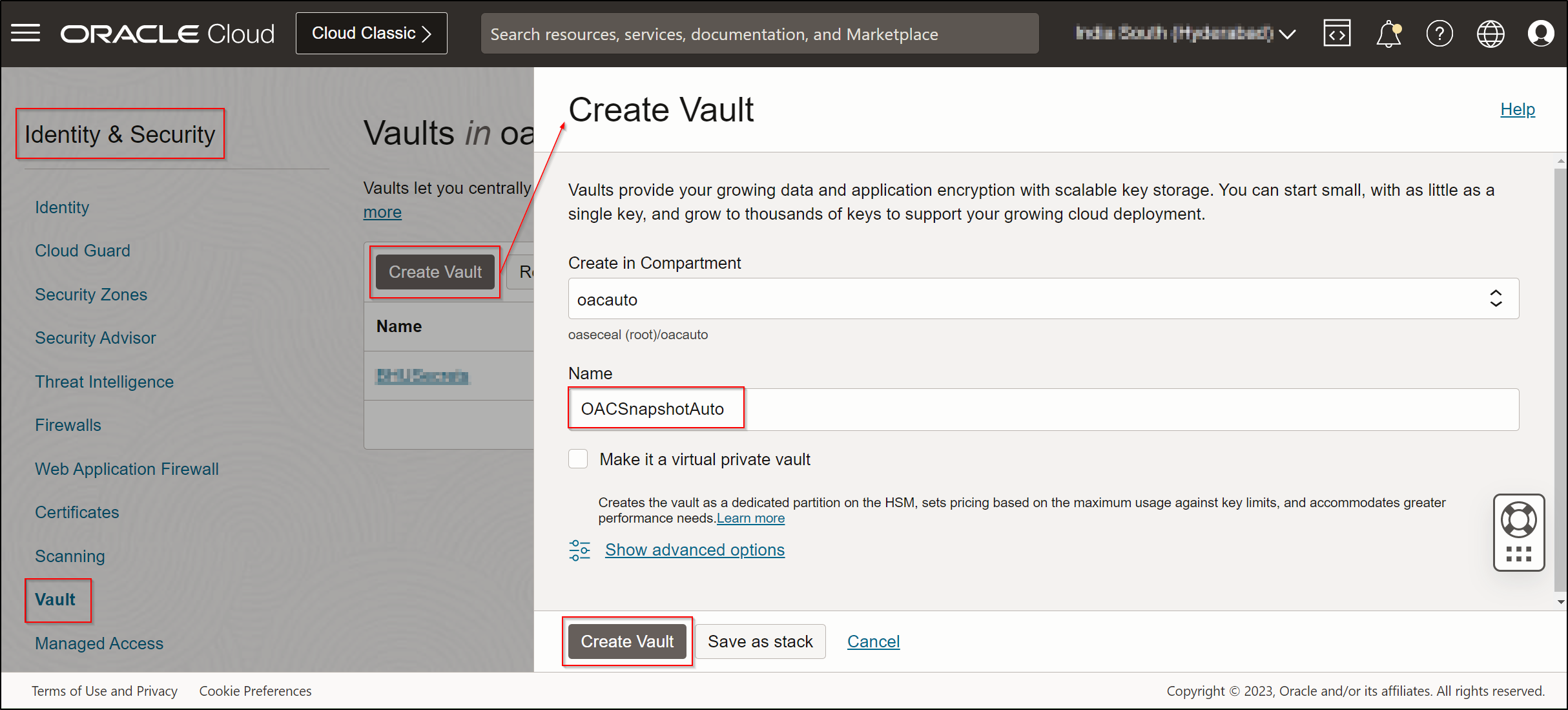
- Create the master encryption key using either the Oracle-provided key or your organization’s provided key.
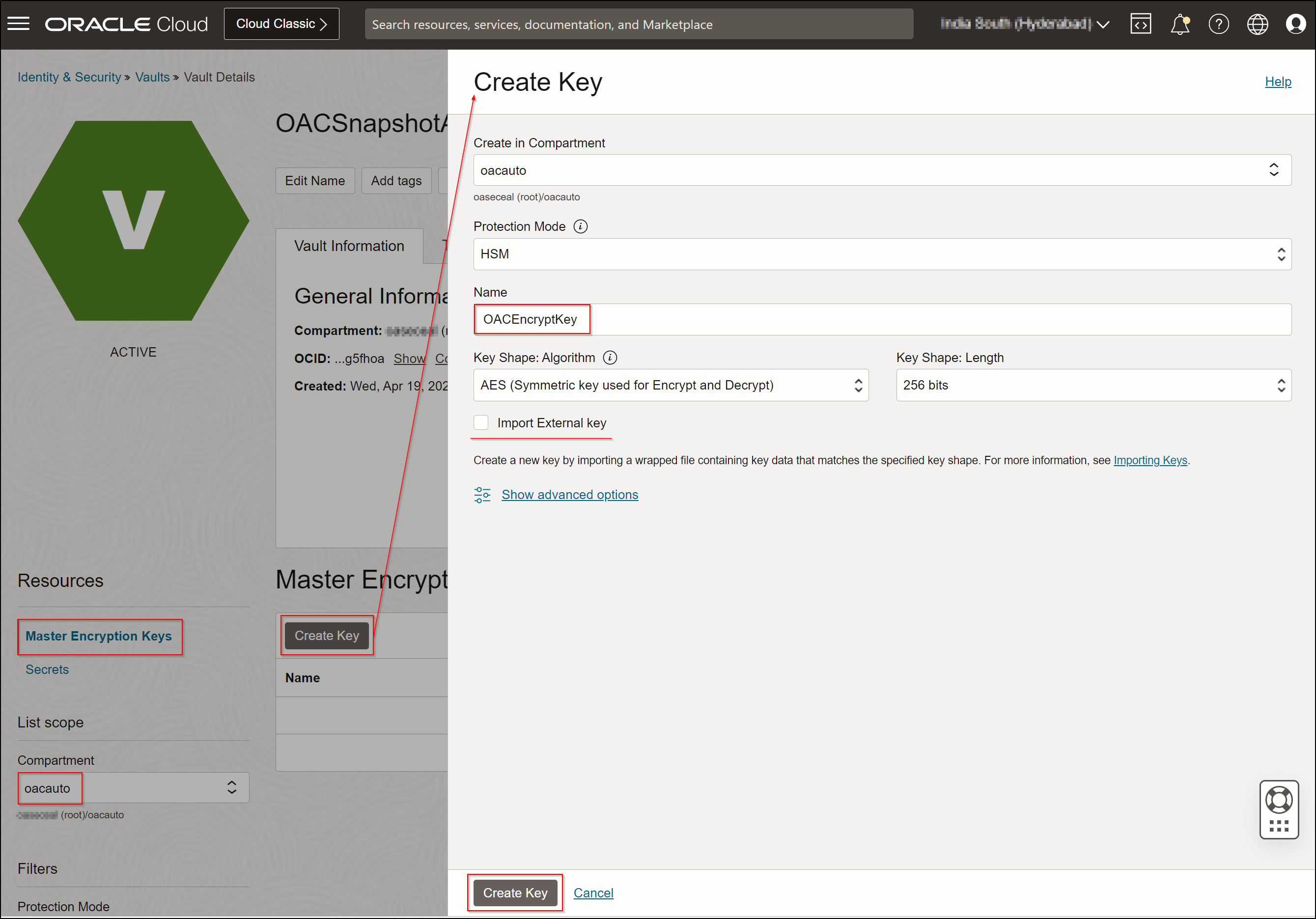
- Create the secret.
Convert the plain text to base64 encoded value and store it in the secret.
command: echo ” ” | base64
command: echo -n clientID:clientSecret | base64 -w 0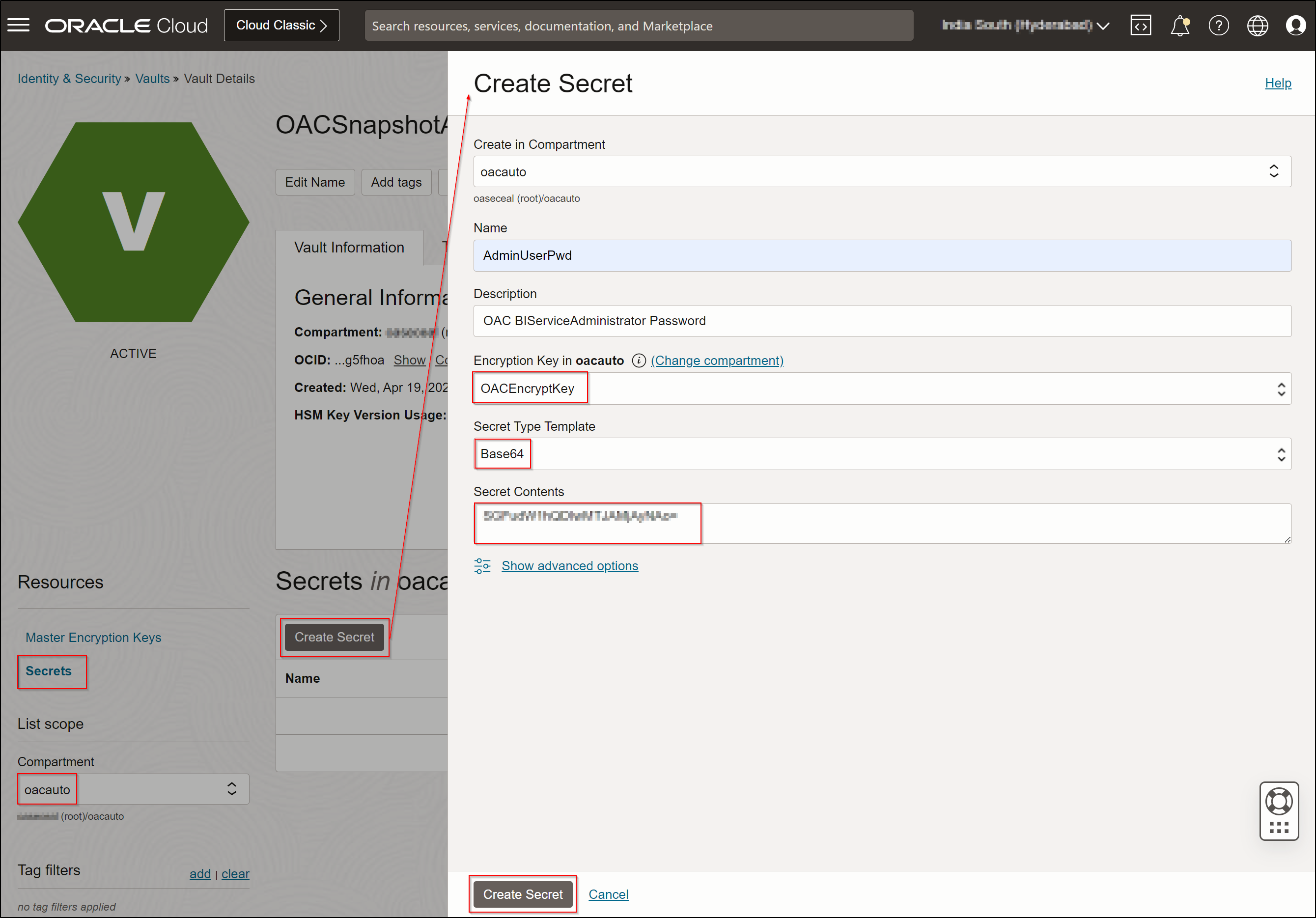
- Get the OCID value of the secret for future use in automation.
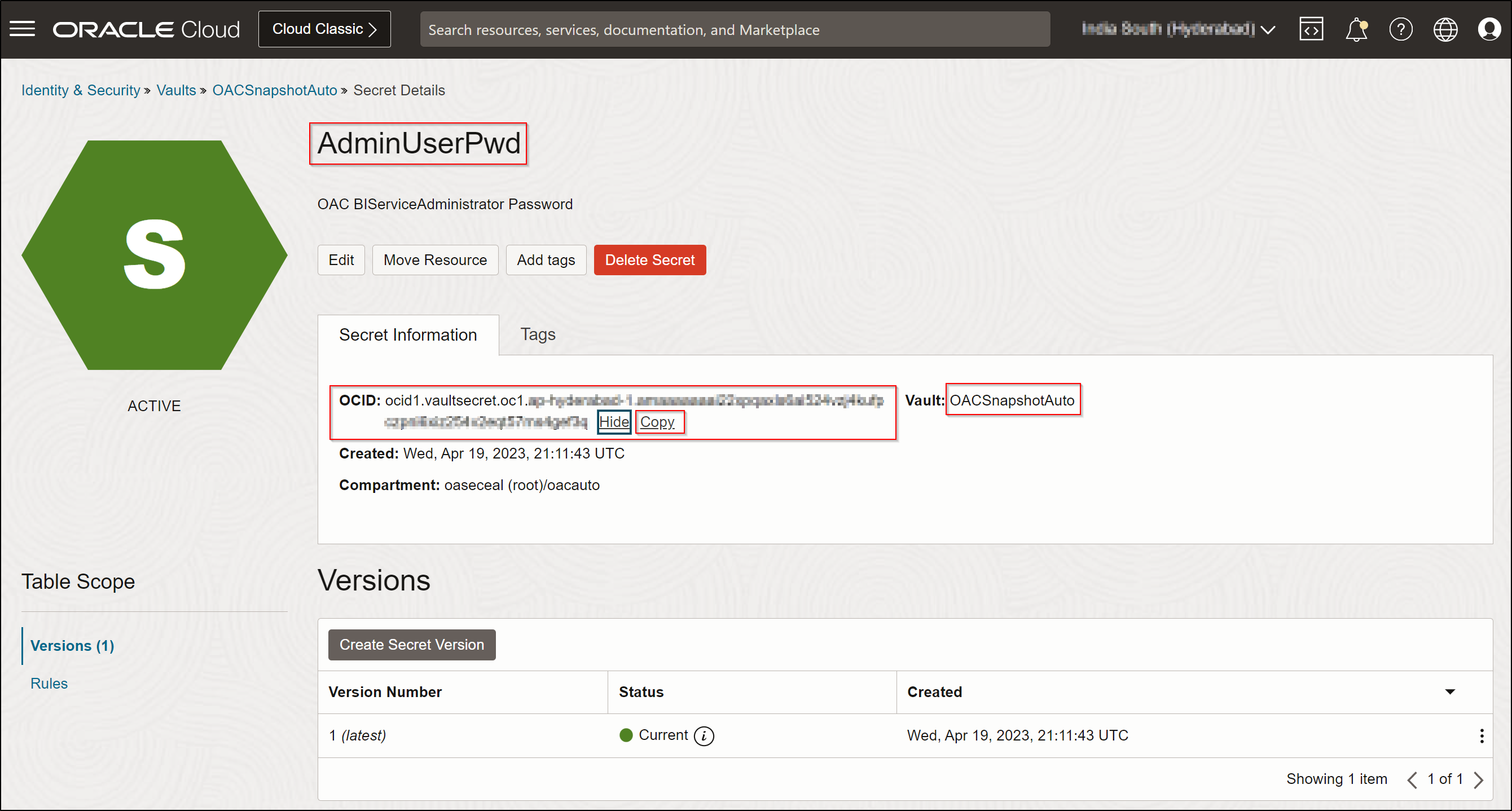
- Repeat steps 6 and 7 for each secret.
Observations
- Convert each value into base64 encoded and stored in a secret.
- To retrieve the secret, extract the base64 encoded value.
- To obtain the plain text value, decode the base64 encoded value.
The following image shows the secrets created in the vault.
Get the OCID of each secret and use those in automation scripts.
The following table lists example values and their formats:
| Secret Name | Value | Stored Value |
|---|---|---|
| AdminUserPwd | Oracle@123@456 | Base64 encoded value is stored |
| AdminUsername | username.lastname@domain.com | Base64 encoded value is stored |
| Bar_Encryption_Password | Admin123 | Base64 encoded value is stored |
| source_AuthBase | echo -n ClientID:ClientSecret |base64 -w 0 | Base64 encoded value is stored |
| target_AuthBase | echo -n ClientID:ClientSecret |base64 -w 0 | Base64 encoded value is stored |
| source_fingerprint | 4b:xx:xx:c2:ba:ca:00:xx:xx:b0:e1:xx:65:xx:7e:a0 | Base64 encoded value is stored |
| target_fingerprint | 4b:xx:xx:c2:ba:ca:00:xx:xx:b0:e1:xx:65:xx:7e:a0 | Base64 encoded value is stored |
| tenancy_ocid | ocid1.tenancy.oc1..axxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx | Base64 encoded value is stored |
| user_ocid | ocid1.user.oc1..axxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx | Base64 encoded value is stored |
Automation script
See the follwoing example code:
# Get the OCID Values of each Secret in OCI Vault.
AdminUserPwd_OCID=ocid1.vaultsecret.oc1.<oci region=””>.amxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxf3q
AdminUsername_OCID=ocid1.vaultsecret.oc1.<oci region=””>.amxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxtra
source_AuthBase_OCID=ocid1.vaultsecret.oc1.<oci region=””>.amxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxmqa
# OCI Profile is the user profile specified in the config file of the OCI CLI (e.g., /home/opc/.oci/config)
OCI_CLI_PROFILE=DEFAULT
# OCI CLI code is defined as shell functions to get the value from the Secret in OCI Vault.
getSecretValue()
{
oci secrets secret-bundle get –profile $OCI_CLI_PROFILE –raw-output –secret-id $1 –query “data.\”secret-bundle-content\”.content” | base64 -d
}
getSecretValueBase64()
{
oci secrets secret-bundle get –profile $OCI_CLI_PROFILE –raw-output –secret-id $1 –query “data.\”secret-bundle-content\”.content”
}
# getSecretValue function gets the value from the secret in a based64 decoded, i.e., in plain text.
# getSecretValueBase64 function gets the value from the secret in base64 encoded, which is stored in secret.
# Call the functions with the respective Secret_OCID value as the argument and assign the value to a variable.
AdminUserPwd=$(getSecretValue $AdminUserPwd_OCID)
AdminUsername=$(getSecretValue $AdminUsername_OCID)
source_AuthBase=$(getSecretValueBase64 $source_AuthBase_OCID)
# Use the variable that holds the value of the secret as a parameter to the script variable.
source_AuthBase=$source_AuthBase
SOURCE_USERNAME=$AdminUsername
SOURCE_PASSWORD=$AdminUserPwd
Call to action
Now that you understand how to read values from OCI vaults and secrets from the shell scripts and use the code to customize scripts to automate the OAC Migration using REST APIs for Disaster Recovery, try it out yourself. See the documentation for OCI Vault and Secrets.

